
Detect Unknown Threats in Early Stages
Uncover more hidden threats in your network with our advanced security intelligence. Progress® Flowmon® provides a more comprehensive view of risks before they escalate.
Launch demo
Respond to Unknown Threats

Advanced AI-Powered Analysis
Employ adaptive baselines and machine learning to uncover potential threat footprints that conventional methods may miss.

Network-Centric Security
Harness your network, the single source of truth in cybersecurity that helps reveal infiltration and attack patterns.

Close the Perimeter x Endpoint Gap
Bridge the gap between network, perimeter and endpoint security that attackers use to evade protection.

Proactive Last Line of Defense
When prevention falls short, leverage early detection and response with insights to reduce the overload of security events to manage.
Bridging the Gaps in Enterprise Cybersecurity
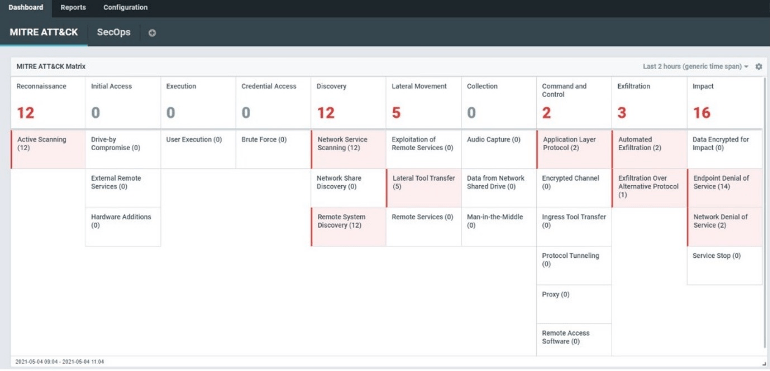
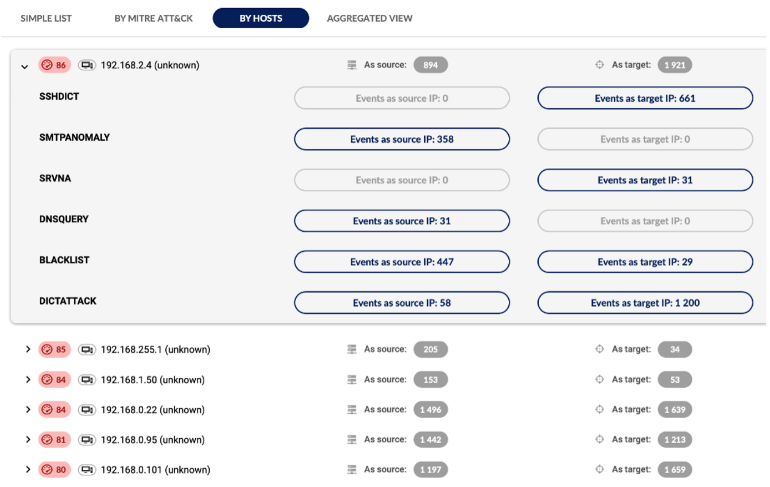
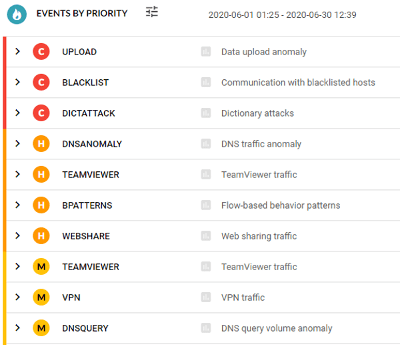
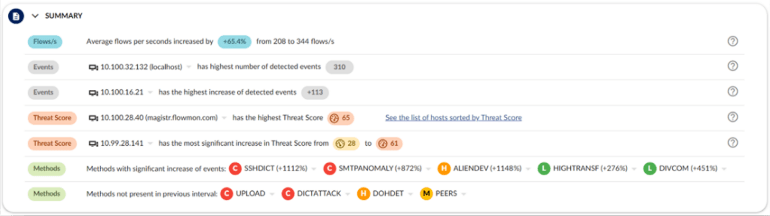
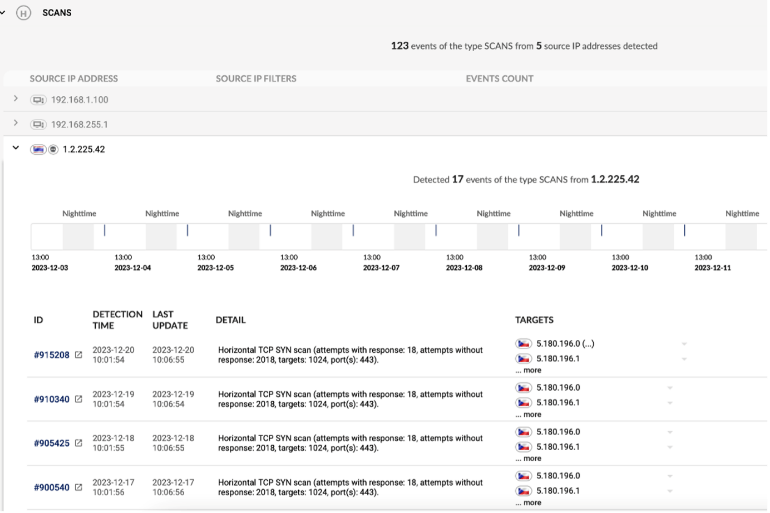
Perimeter security is primarily designed to block external attacks, while endpoint security focuses on protecting individual devices. However, endpoint security often fails to cover up to 50% of network-connected devices, creating substantial vulnerabilities. Network-level detection fills this gap, monitoring both internal and external threats across your IT environment and device types. Combining AI with signatures, Flowmon identifies many indicators of compromise (IoC), crucial for early warning at every stage of the attack lifecycle, from infiltration to reconnaissance and data exfiltration.
Expose Attacks Before It Is Too Late
Improve your cybersecurity resilience with Flowmon’s powerful features.
Resource Library
Check out these resources to help you get started with Flowmon.