Flowmon Packet Investigator Automated PCAP Analyzer & Capture
Flowmon Packet Investigator (FPI) is a network traffic auditing tool that automatically records and analyzes full packet data. Combining automated PCAP analysis and built-in expert knowledge, it provides you with an instant deep understanding of emergent issues and offers suggestions for a remedy.
Locate the root cause
Autonomous investigation of DHCP, DNS, FTP, IMAP, IMF, POP, SIP, SLAAC, SMB, SMTP, IP, TCP, SSL, HTTP.
Reduce MTTR
Let the analytical engine locate the root-cause, describe it and recommend a solution.
Record your traffic
On-demand and on-event L2-L7 network traffic recording (packet sniffing).
Discover 3 unique use cases of Flowmon Packet Investigator
Watch the webinar: Mastering Performance Optimization: A Deep Dive into Troubleshooting with Flowmon
Instant pcap analysis
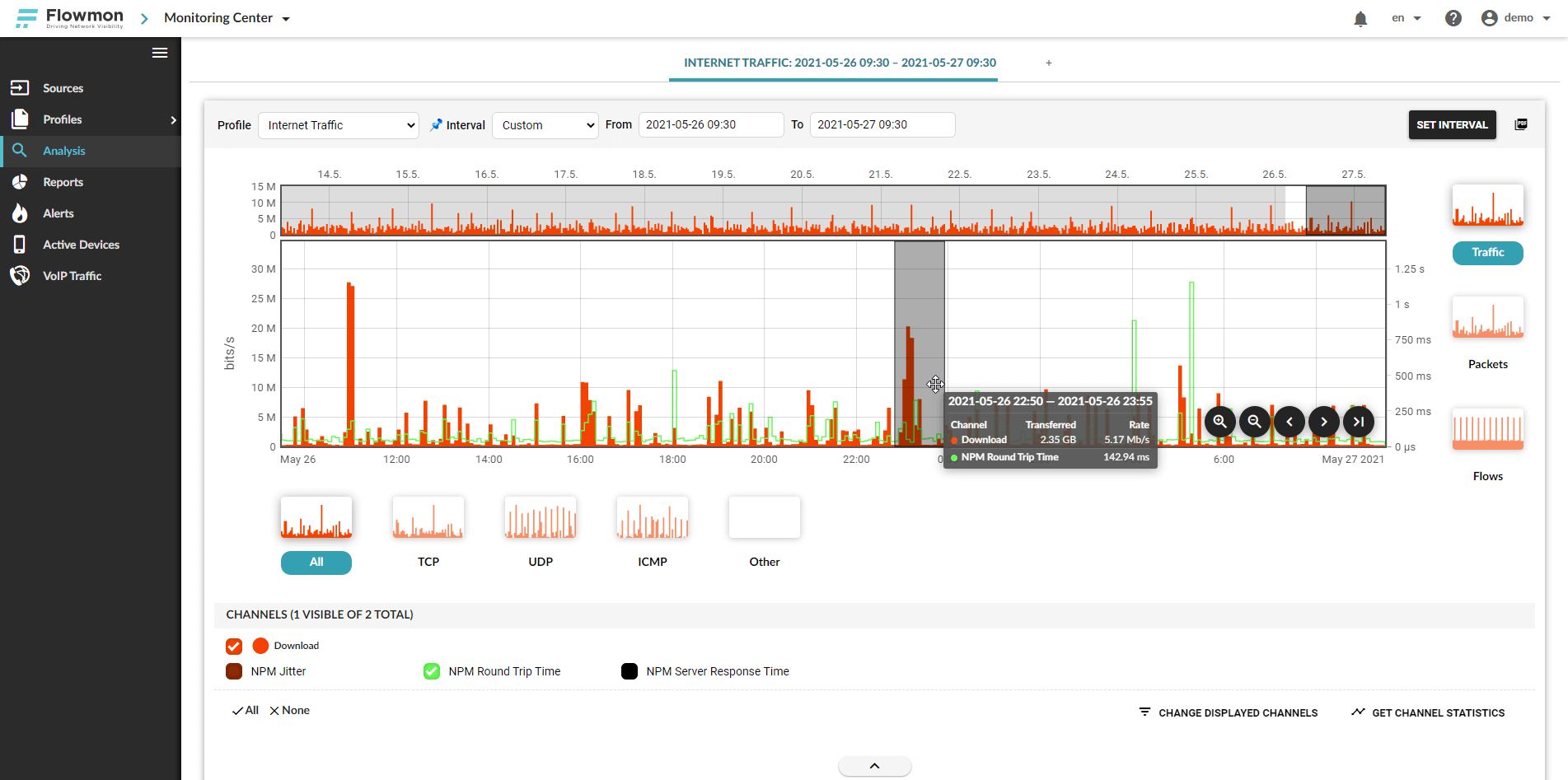
The PCAP Analyzer by Flowmon Packet Investigator performs an automatic decision-tree analysis of network protocols, their dependencies, RFC specifications and errors from a PCAP file, giving you an immediate number of issues found as well as their severity.
Built-in expertise
The FPI houses decades of combined networking experience provided by our in-house experts. By expanding the analysis results, you can browse through the individual analysis steps and see explanations of the possible root-cause of issues including recommendations for remedial action.
Automatic capture
Never drop a packet with the PCAP Analyzer. You can record packets manually, upload your own PCAP files or the FPI can performed automated policy-based packet capture, e.g. upon security event detection, at speeds of 1G–100G. The rolling buffer retains a number of packets from before the event occurred, making sure that no history is lost.
Functional versatility
The PCAP Analyzer by FPI is built to cover a broad spectrum of protocols with the number constantly rising. Identify malfunctions or misconfigurations of critical network devices (ARP, DNS, DHCP, ICMP, NTP), expose client/server encryption incompatibility (SSL/TLS version, encryption algorithms, certificates), application protocol stack issues (HTTP, Samba, FTP, IMAP, POP, etc.) or IoT issues (CoAP, IEC104, GOOSE, MMS, MQTT).

"Flowmon Packet Investigator helps us to automate troubleshooting, which means we can spend less time in Wireshark PCAPs. Instead of going through packets manually, we know immediately what kind of issue we are dealing with and what the root cause is. And because we don't need deep knowledge of network protocols to use it, packet analysis is made available to every member of our IT team."
IT Center Coordinator
Speed up your Wireshark investigation
The FPI is like an extra team member.
| Packet Investigator | Wireshark | |
|---|---|---|
Required skill set | Operator, Junior admin, L1 engineer | Analyst, Senior admin, L2/L3 engineer |
Primary use case | Automated root cause analysis | Manual troubleshooting, forensic analysis |
Packet capture | Monitoring appliances, 1G/10G/40G/100G | Diagnostic laptops, hosts, usually 1G |
Capture control | Central control and scheduling | Manual on individual locations |
Automation | Triggered capture & REST API | None or homegrown scripts |
Stages of Automated PCAP Analysis
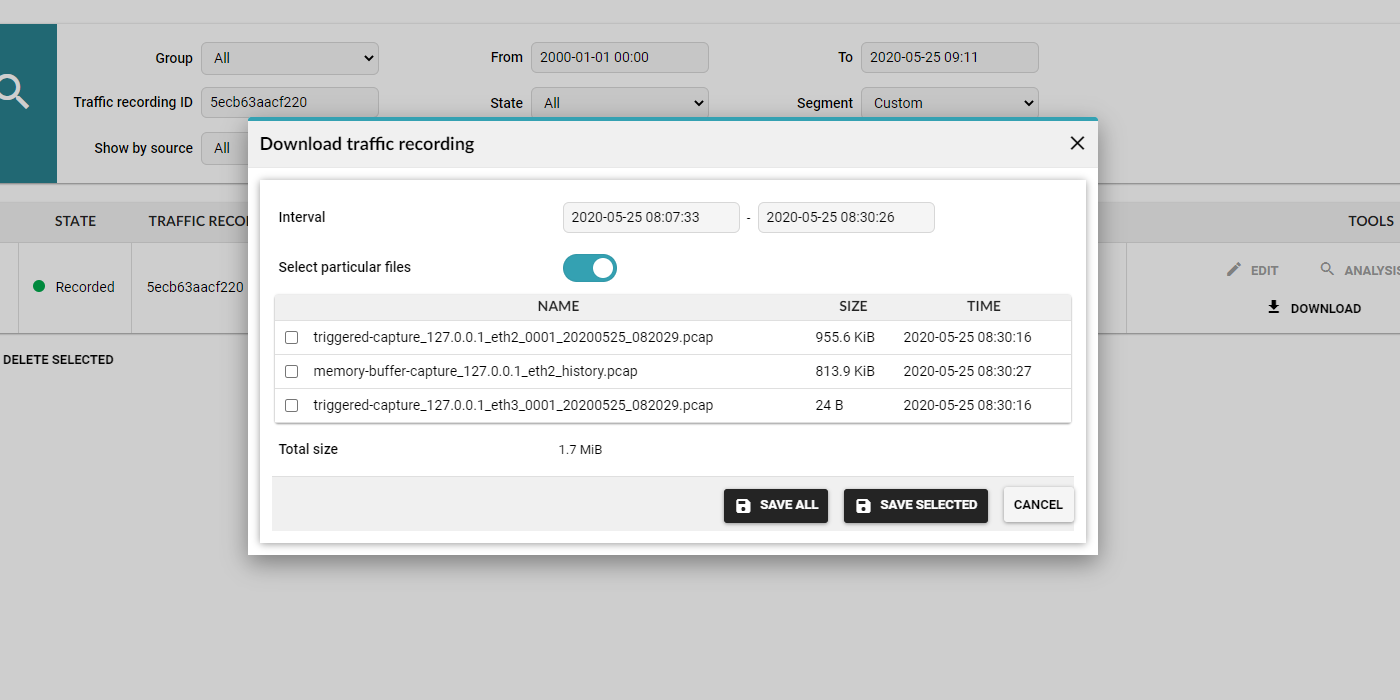
1. Getting the data
The FPI captures full-packet traces on-demand via automated, manual, and scheduled triggers, or lets you upload your own file.
2. Analyzing the PCAP
The analytical engine investigates the packet traces via an intelligent decision-tree analysis.

3. Looking for errors
The FPI looks for RFC deviations and unexpected occurrences and translates the errors into intelligible explanations.

4. Visualizing the results
You can see the number and severity of issues located with the option to view the full analysis right away.

Get in touch
Do you have question around the solution or want to schedule a call. Write us a message.
Contact usRequest free trial
Get no-obligation 30-day trial of Flowmon in your network.
Get your trial todayRead more about the Packet investigator
Flowmon Packet Investigator Models Specification
Flowmon Packet Investigator Brief