Network Anomaly Detection and Network Behavior Analysis
The rise of unknown malware compromising internal systems, devastating DDoS attacks, APTs and threats bypassing traditional security have changed the IT security landscape. Building perimeter walls and relying on signature based solutions is not enough anymore. Only a detailed awareness of network behavior and a proactive fight against cyber threats can give control over the IT environment back to administrators.
Launch demoProactive security to reveal threats undetectable by other technologies
Most companies rely on legacy IT systems, consisting of perimeter security and endpoint protection. However, they dismiss the significant infrastructure located between these two areas. In the world where threats have more opportunities than ever to bypass traditional solutions and sneak in, where 70% of attacks come from an internal network, this approach is not enough anymore. How do you secure your systems and data from ever changing threats that bypass traditional solutions?
The answer to this challenge recommended by respected authorities such as Gartner is a proactive detection and mitigation of network anomalies and undesirable behavior provided by Network Behavior Anomaly Detection. NBAD solutions permanently observe network traffic, analysing communication to seek anomalies and reveal suspicious behavior. This enables a response to yet unknown security threats undetectable by other technologies.
NBAD delivers advanced technology to:
Have a detailed awareness
of what is happening in the network to detect and respond targeted attacks, botnets, unknown malware, insider threats, data leakage, etc
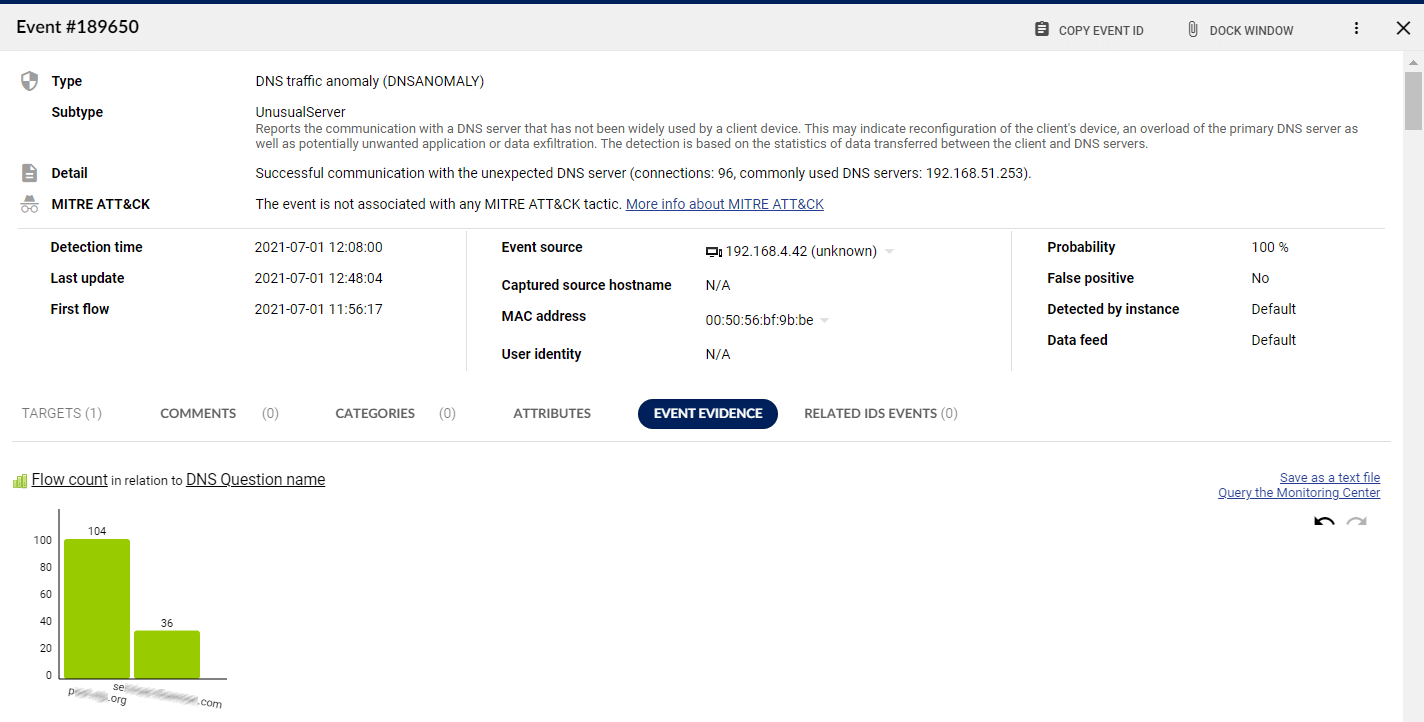
Utilize network traffic statistics
exported by routers/switches or network probes (NetFlow, jFlow, IPFIX, NetStream and other flow data standards) to detect malicious behavior.

Complete the security circle by a complementary Network Detection & Response solution
Extends log management and end-point protection with network detection and response to get a full visibility across complex IT environments (SOC Visibility Triad approach).
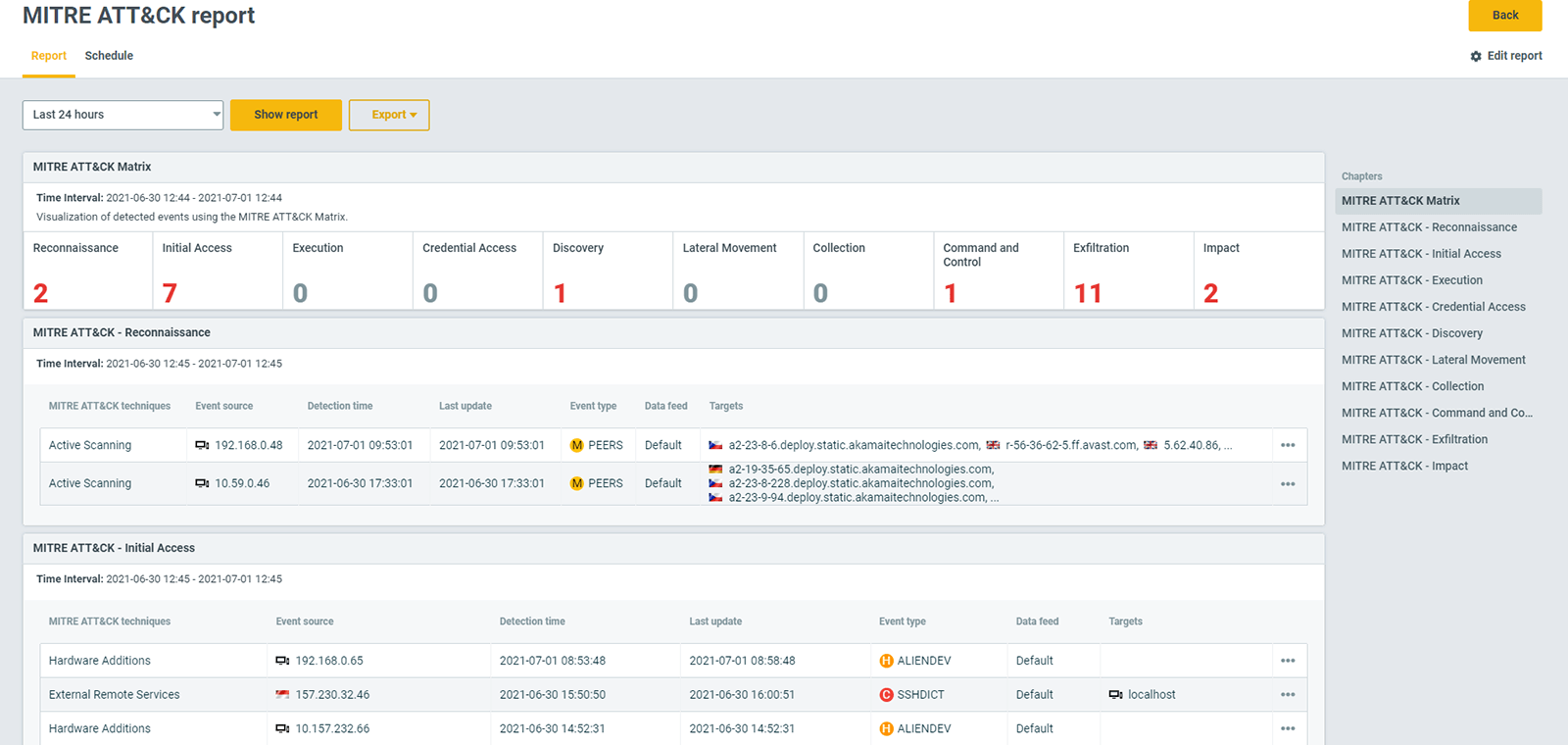
Streamline network operations
by the automatic detection of anomalies and operational issues.

Flowmon ADS - Gartner recognized network behavior anomaly detection
Flowmon delivers to businesses an advanced security intelligence based on NBAD technology. Its Flowmon Anomaly Detection System (ADS) is a powerful tool trusted by CISO and security engineers globally providing them with dominance over modern cyber threats. The solution utilizes sophisticated algorithms and machine learning to automatically identify network anomalies and risks that bypass traditional solutions such as firewall, IDS/IPS or antivirus. Learn more about anomaly detection.

"After you have successfully deployed firewalls and intrusion prevention systems with appropriate processes for tuning, analysis and remediation, you should consider NBA to identify network events and behavior that are undetectable using other techniques.“
VP at Gartner
Request free trial
Get no-obligation 30-day trial of Flowmon in your network.
Get your trial today