Retrospective analysis
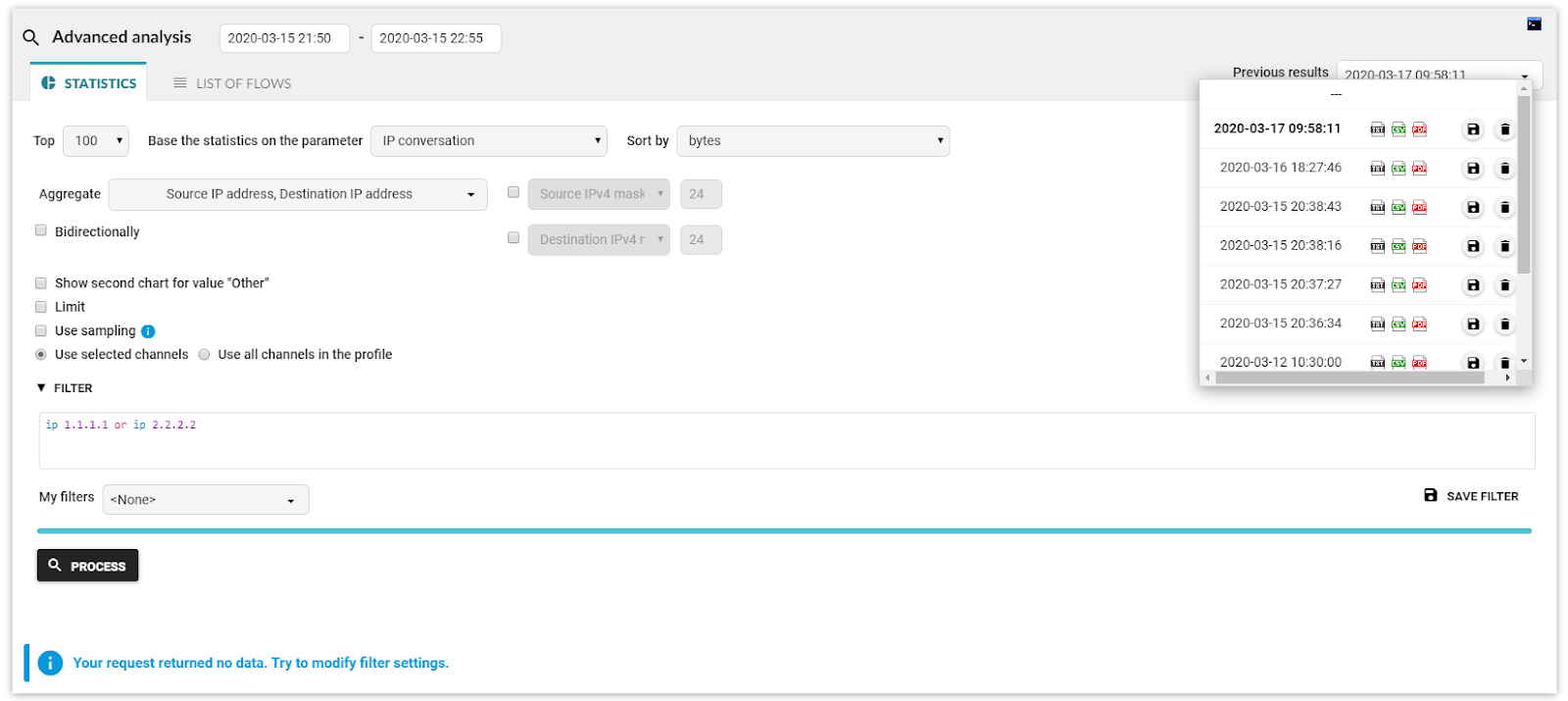
Use the Analysis feature in the Flowmon Monitoring Center. Select the “All sources” profile to make sure you do not miss any traffic. You may select a specific time interval to focus on the desired period. This can be hours, days, or even weeks. The best aggregation for this purpose is “IP conversations” and “Top 100”. Add a filter for IP addresses that you would like to validate. You can filter multiple IP addresses simultaneously by combining them using the OR operator. You can also filter by any attribute of the collected network telemetry, so adjust your query when IoCs are more complex. Then, run your query. This can take some time depending on the amount of traffic that needs to be analyzed to get your result. You do not have to wait; the query will run in the background and you will pick your results later.
Figure 1: Query for IP conversations with IP address 1.1.1.1 or IP address 2.2.2.2 showing no data, which is a sign that there was no communication with those IP addresses in your network.
Proactive detection
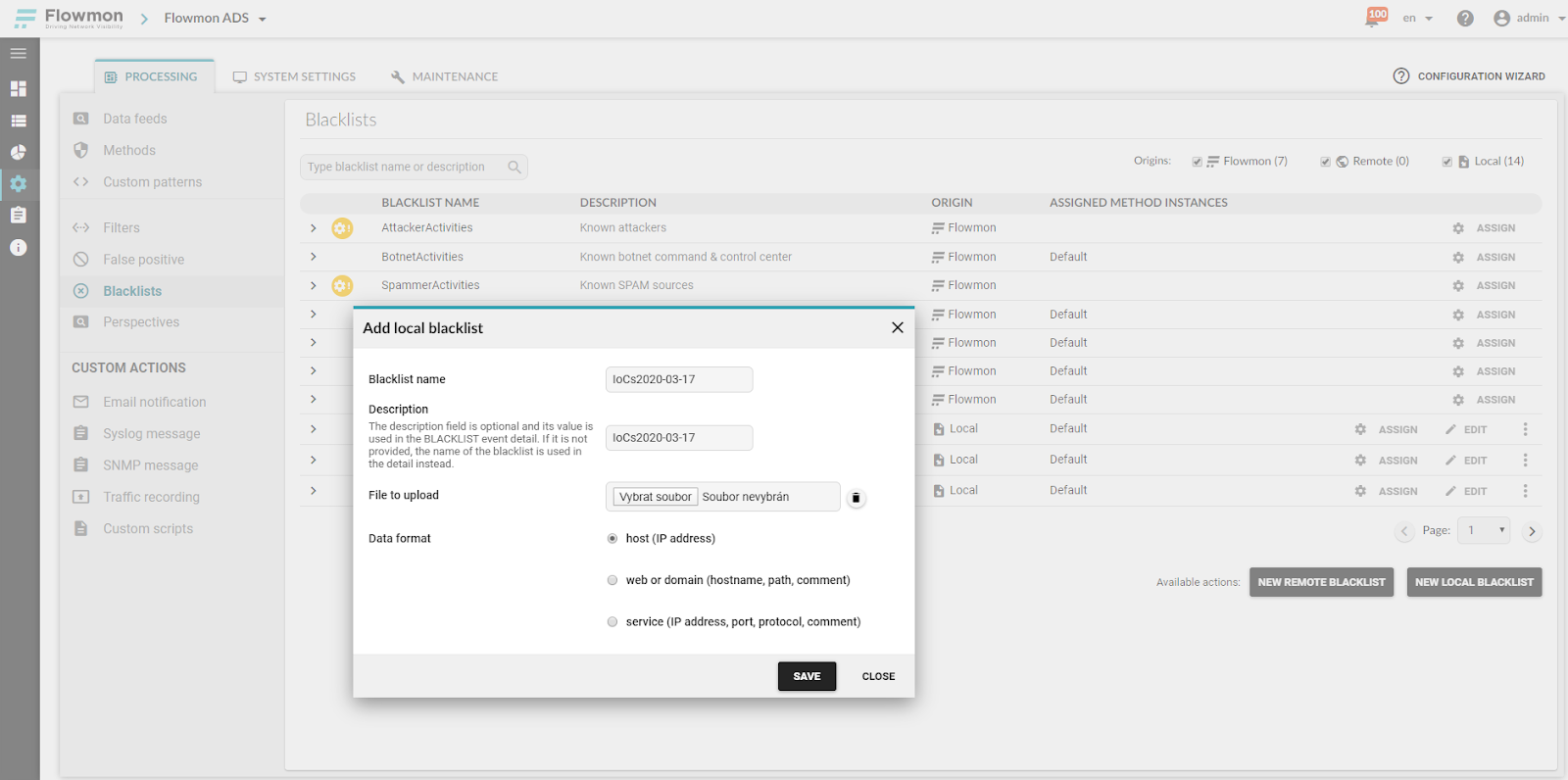
You can use the “Custom Blacklist” feature in Flowmon ADS to introduce a specific list of malicious IPs (or domains). ADS will use this list of malicious IPs or domains to validate your traffic in real time. When there is a match, a corresponding event of the BLACKLIST type is generated. Create a simple text file with each IP address on a single line. Go to Flowmon ADS, Settings, Blacklists and create “New local blacklist”. Provide a name for the blacklist and a description that will be part of the event details and upload the file.
Figure 2: Adding a new local custom blacklist
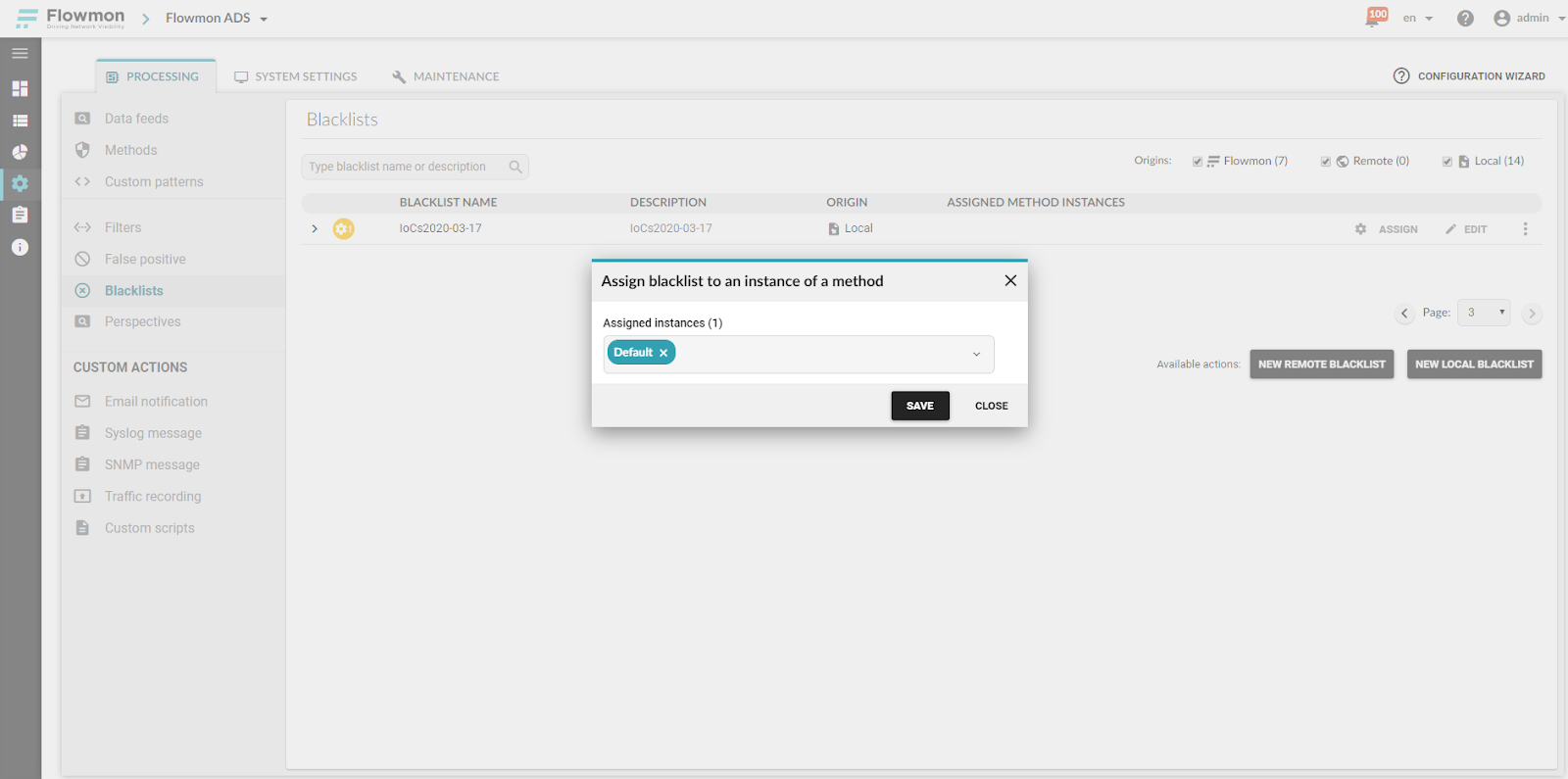
Do not forget to assign the new custom blacklist to instances of detection methods in order to apply it on the data.
Figure 3: Assigning a local custom blacklist to instances of detection methods
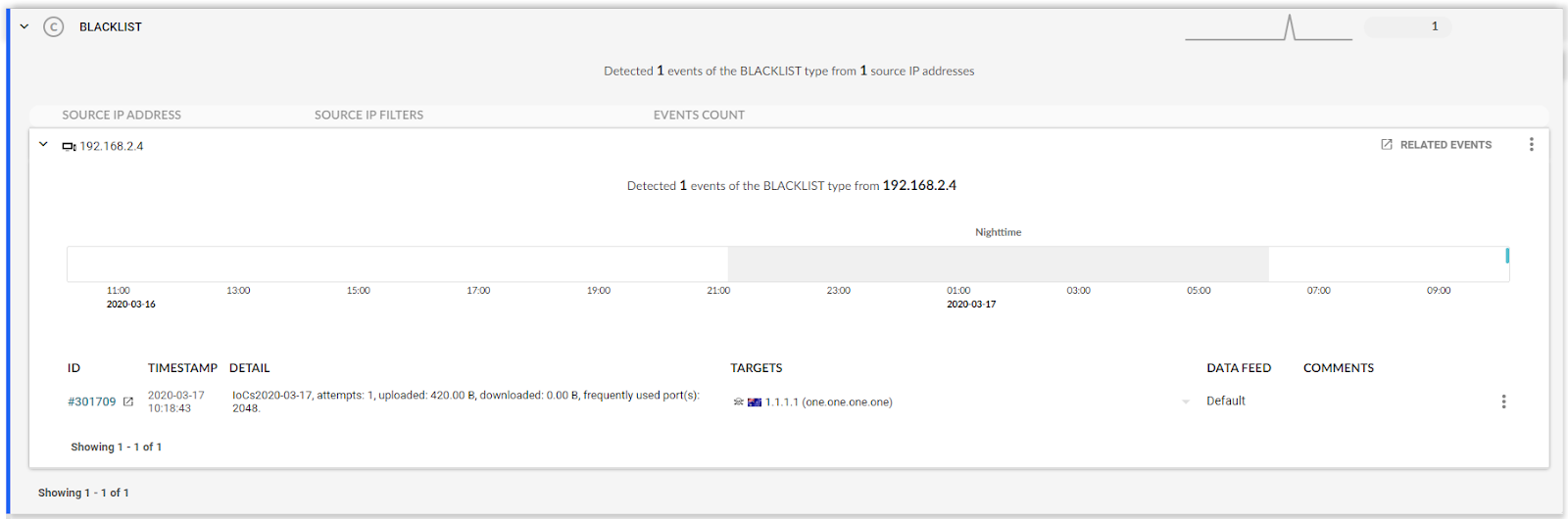
Any communication with a malicious IP address is reported as an event showing an internal IP address that communicates with an IP address included in the list of IoCs. You can use standard event notification mechanisms (event reporting, syslog, etc.) and actions such as triggered packet capture as a response to the event.
Figure 4: Event detected based on a custom blacklist; in this case just a ping command to IP address 1.1.1.1 previously included in the custom blacklist for demonstration purposes
Flowmon ADS has built-in reputation feeds from various sources that include more than 1 million malicious IPs or domains, such as botnet command & control, sources of malware, etc. The detection of this kind of malicious communication works out of the box together with behavior-based anomaly detection methods to report on malicious activity in the network.
In case of need, feel free to contact Flowmon technical support at support@flowmon.com for assistance with the configuration or data analysis.