At the outset, it is worth explaining the differences between SCADA and ICS, as these two terms are frequently used interchangeably by the professional public, engineers in the field of industrial control systems, and the public. The best explanation is that SCADA generally refers to control systems encompassing large geographic areas, such as systems of gas pipelines, the transmission of electric power or water distribution. ICS is the technically correct term to use, but only if we mean all types of industrial automation.
It is helpful to use both terms together because the term SCADA is better known in the professional press, among journalists, civil servants, and the public. SCADA in point of fact is a discipline within ICS.
Examples of ICS systems
| Discipline | Example Verticals | Standard Control Devices |
|---|---|---|
| Process Control | Rafinery | Distributed Control System (DCS) |
| Discrete Control | Automotive | Programmable Logic Controller (PLC) |
| SCADA (Wide Area Control) | Pipeline | Master Terminal Unit (MTU)/Remote Terminal Unit (RTU) |
In recent years, ENISA (European Union Agency for Network and Information Security) has been preparing strategies and directives in the field of cyber security of critical and important information systems, where SCADA/ICS unequivocally falls under. The final "product" of this directive is to implement forms of law on Cyber Security of the member states of the European Union.
Three types of security risk for SCADA/ICS
A cyber-attack targeting the SCADA/ICS environment can have really devastating consequences. Imagine the end result of an attacker who has carried out cyber espionage over many months. The attacker is now capable of using the data collected about the individual parts of various systems, e.g. to shut down energy, gas and water, to blackmail or, in the case of military conflict, to malfunction and destroy critical infrastructure. The results can lead to disaster (even to the loss of human life).
There are basically three types of security risk: external - APT (targeted attacks), internal (employees and contractors with access to infrastructure), and finally, human factor failures. With APT/targeted attacks, this concerns specially written malicious code (malware, exploits), which may be spread throughout the industrial network as a botnet. This is a specific case. But when it occurs, system admins do not have the tools to detect the threat instantly. Notice, that he most security incidents and types of attacks were classified only after forensic analysis had been carried out, after additional identification (using signatures of “antivirus” databases), often downtime, or the malfunction of critical systems.
Security attacks always appear in two main forms: industrial espionage and/or destruction.
Examples of attacks over the last years
| Year | Malicious Code/Type of Attack | Target Attack | Functionality / Motivation | Security Incident |
|---|---|---|---|---|
| 2009 | Night Dragon | Exxon, Shell, BP | Remote Access Trojans (RATs) / Data leakage and industrial espionage | N/A |
| 2010 | Stuxnet | Iran Natanz nuclear programme | Capture and execution of changes in the data read and written to the PLC / Destruction | Malfunctioning (DoS) 1/5 centrifuge |
| 2014 | Blacken | N/A | Distributed Trojan ICS/SCADA software downloaded from compromised producer’s, scanning of LAN to get information from OPC servers and reverse communication on the C&C server/data leakage and industrial espionage | N/A |
| 2015 | Black Energy | Ukrainian power grid | Malware distributed through phishing activities, with reverse communication with the attacker via remote control / Destruction | Malfunction of electric power distribution for 8000 customers |
Reconnecting two worlds
Operational Technology (OT) in ICS had long been separated from the traditional computer networks in the IT environment. As a result, they were secured against classic cyber-attacks. Great emphasis was placed especially on the physical security of systems in geographically separate locations. But nowadays, apart from the high-security of these systems, interoperability and mobility are also both required. The result is that separate systems and devices, using proprietary protocols, can now connect to the familiar computer networks that use the TCP/IP protocol for the transfer and exchange of information (Modbus Protocol). From these networks employees can, by using terminal equipment, access the internet which "opens the door" to different types of security attacks, and with the implementation of IoT (e.g. smart metering) it is relatively simple for an attacker to compromise the device by botnet from anywhere.
A few examples
Although it is very difficult to carry out a cyber-attack on terminal systems, experience shows us these organisations lack a detailed implementation of information security and technology security processes. The ICS OT environment is indeed separated from traditional enterprise IT and internet access by a group of firewalls. Nevertheless, they are often outdated or limited in terms of visibility, and an attacker has the possibility of getting "inside". A good example is the aforementioned Blacken or Black Energy malicious codes. The common denominator is phishing.
In 2015, the computers of an unnamed water company were attacked by usage of the unpatched vulnerability on their website, which served as a communication pay portal for the company’s customers. It was through SQL injection and phishing, during which the login information for the control system were stored on the front-end web server. The system connected to the internet in this way allowed the attacker to control PLCs, and afterwards, the attacker could change the flow of water and its chemical composition.
Researchers from GIT (Georgia Institute of technology) created ransomware with the task of "keeping in check" critical systems of water treatment plants. The next logical step is of course compromising PLCs. An attacker simply bypasses the firewall through phishing, undermining the PLC that forces a connection to the internet and back through the firewall to communicate with the attacker (e.g. via C&C server).
Figure 3: Attacker infiltrating SCADA environment
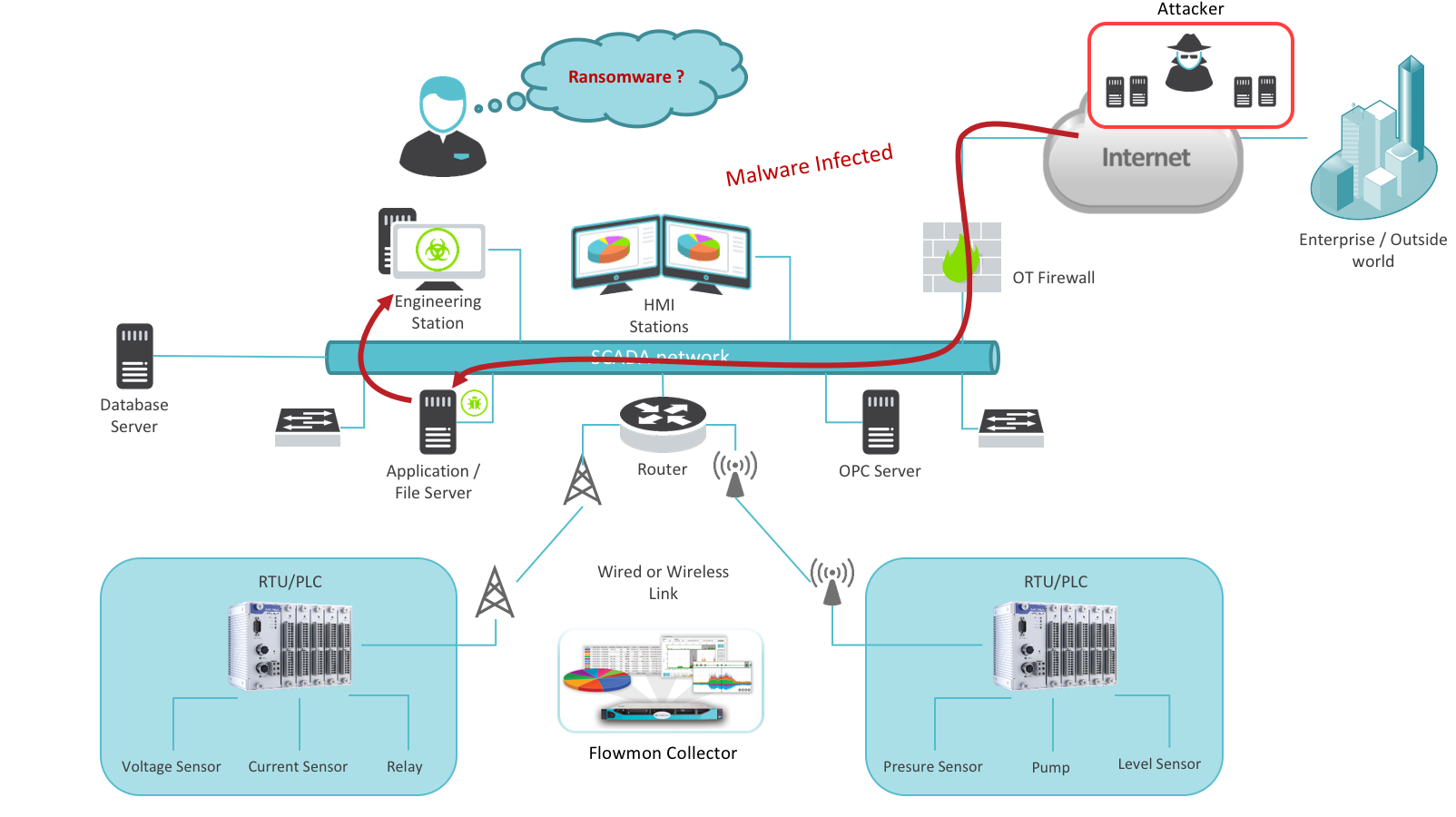
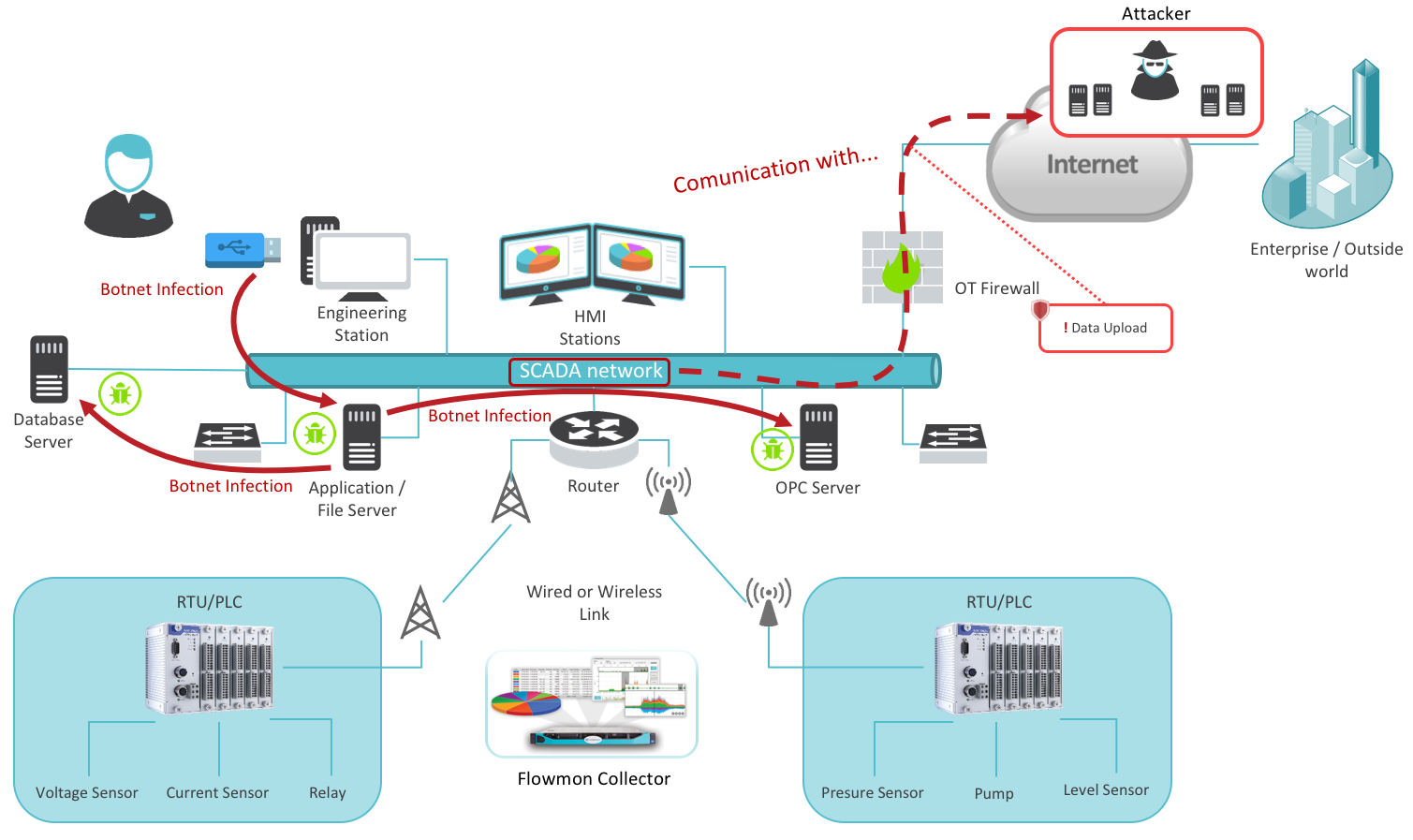
Another weakness may be the introduction of malicious software "from the inside" via media connected to the network (laptop, USB, etc.). Malicious software can communicate with a remote attacker even easier. This eventually leads to the acquirement of information about various systems or non-secure terminal equipment. An example of this is the much talked about Stuxnet worm, designed to attack Siemens ICS. At the height of its fame in 2010, it exploited an unknown vulnerability in the Windows OS and through a compromised USB device spread between computers. When a computer was infected, Stuxnet used the default password to access PLCs systems functioning for WinCC and PCS 7. An attacker could thus take control of PLCs through the C&C servers and then reprogram them for a specific purpose. Industrial espionage in this case is always the first step towards a possible successful attack, which can cause a malfunction or destruction of physical infrastructure.
Figure 4: Botnet compromising SCADA system via infected USB disc
Security risks in the SCADA/ISC environments
- Non-secure / or few secure end points
- Irregular patching of IT systems
- Obsolete equipment and OS
- Absence of network visibility
- Absence of technological security design and processes
Simplified course of security events
- Penetration of the network (phishing, transfer of media, exploits)
- Movement of attacker across network and collection of information
- Attack (deleting logs, configurations, gaining control over the system)
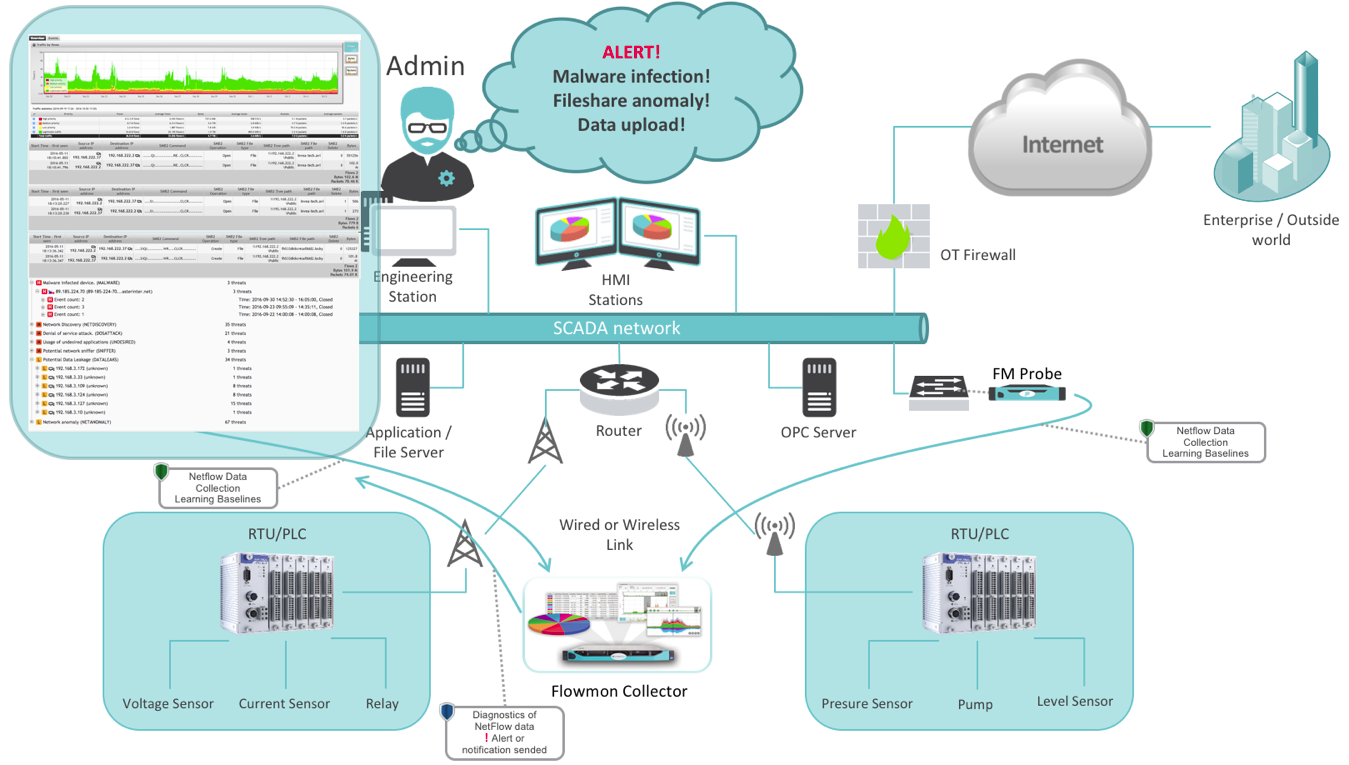
Network visibility is crucial for ICS security
All the attacks have a common denominator – if new sophisticated methods had been used, these only came to light after the forensic analyses. This resulted in the leakage of data, industrial espionage, malfunction or destruction of physical infrastructure. Monitoring and visibility into network communication in industrial networks, the collection of statistics, their retention, analysis, and notification enables a way to identify security events in the time of their creation.
We can't protect what we don’t see. Visibility into industrial networks is the key factor for the safety of the ICS. In the enterprise environment of computer networks, data flows are very variable. Services there use many protocols and ports. The advantage of SCADA/ICS networks lies in more or less stable data flows. Thus it is possible to quickly detect and respond to each deviation (anomaly) and reduce rapidly the MTTR (Mean Time to Resolution), which is a fundamental aspect for building rapid prevention. These should include a similar safety design and processes that are implemented in the enterprise environment regarding the different needs of SCADA/ICS. An elegant solution is high-quality monitoring based on visibility into industrial networks, and detecting anomalies as soon as they occur.
Figure 5: Admin controls communication in SCADA environment via network monitoring tool