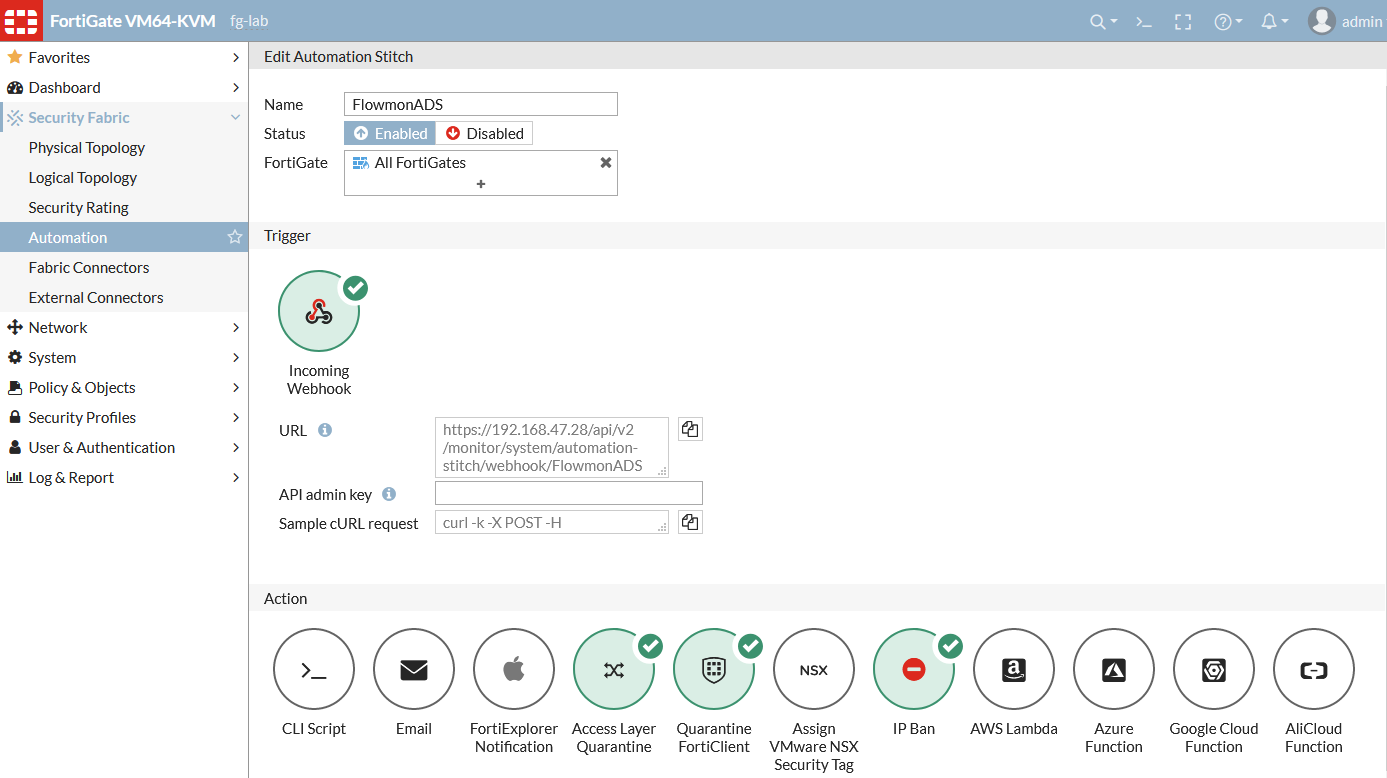
This led us to revise our integration script to utilize this functionality and allow administrators to easily configure different levels of mitigation with the webhooks. All this is done in the FortiGate configuration of Security Fabric automation and is used for authenticated HTTPS calls that allow us (as a third party) to pass IP and MAC address and configure an action to be triggered by this call.
Typical response actions following unwanted traffic detection:
- IP Ban
- Access Layer Quarantine
- Quarantine FortiClient
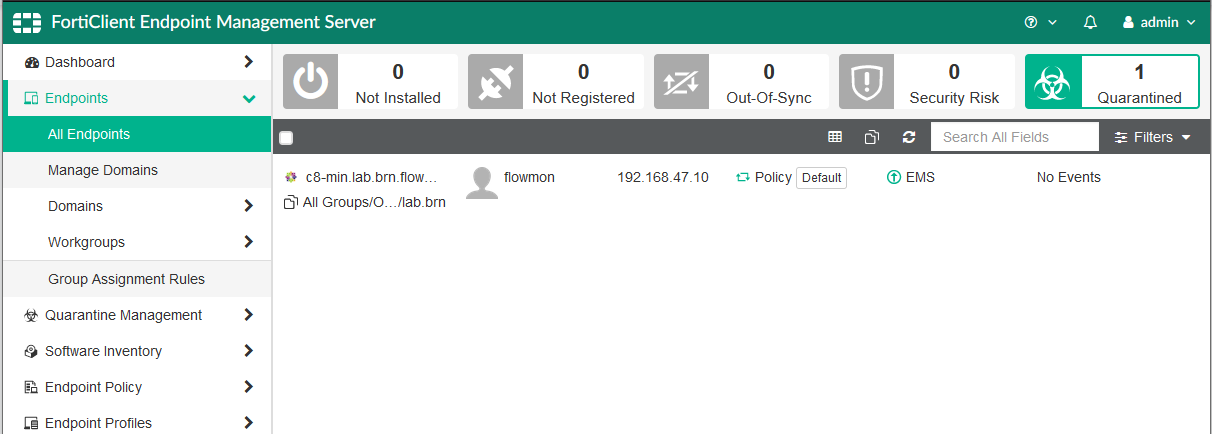
There is one more improvement allowing Access Layer mitigation in cases where Security Fabric controls a switch or WiFi controller and can quarantine MAC addresses of infected stations. When FortiClient EMS is deployed, you can also use the FortiClient quarantine action.
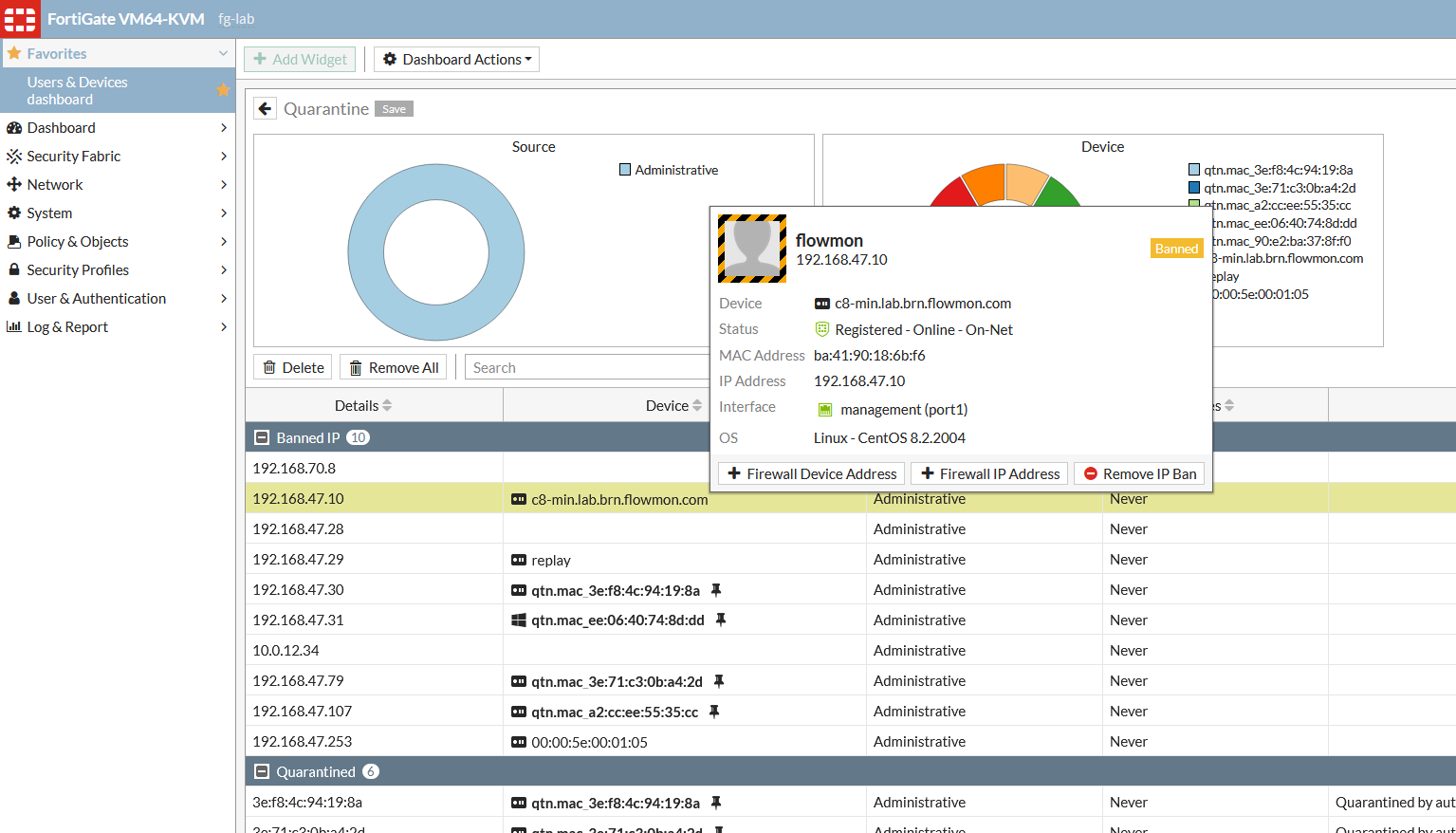
This again helps to automatically stop any potential infection from spreading when these control functions are used.
In addition, it allows you to easily configure which action should be taken once our Anomaly Detection System (ADS) detects a threat without having to script all the functionality there.