We have redefined the scalability and usability of the flow monitoring system for future proofing network operation tasks. A single Flowmon installation can scale to millions of flows per second and tens of independent locations with distributed architecture controlled from a single console. The revised user interface brings remarkable user experience while retaining the same philosophy of workflow and feature set. Encrypted Traffic Analysis brings unprecedented visibility into SSL/TLS traffic, leaving packet analysis tools behind in use cases, such as malware discovery. Furthermore, native visibility into the IoT/ICS environment extends our use cases beyond IT operations and network security.
https://www.youtube.com/embed/g3IFu1qKMmA
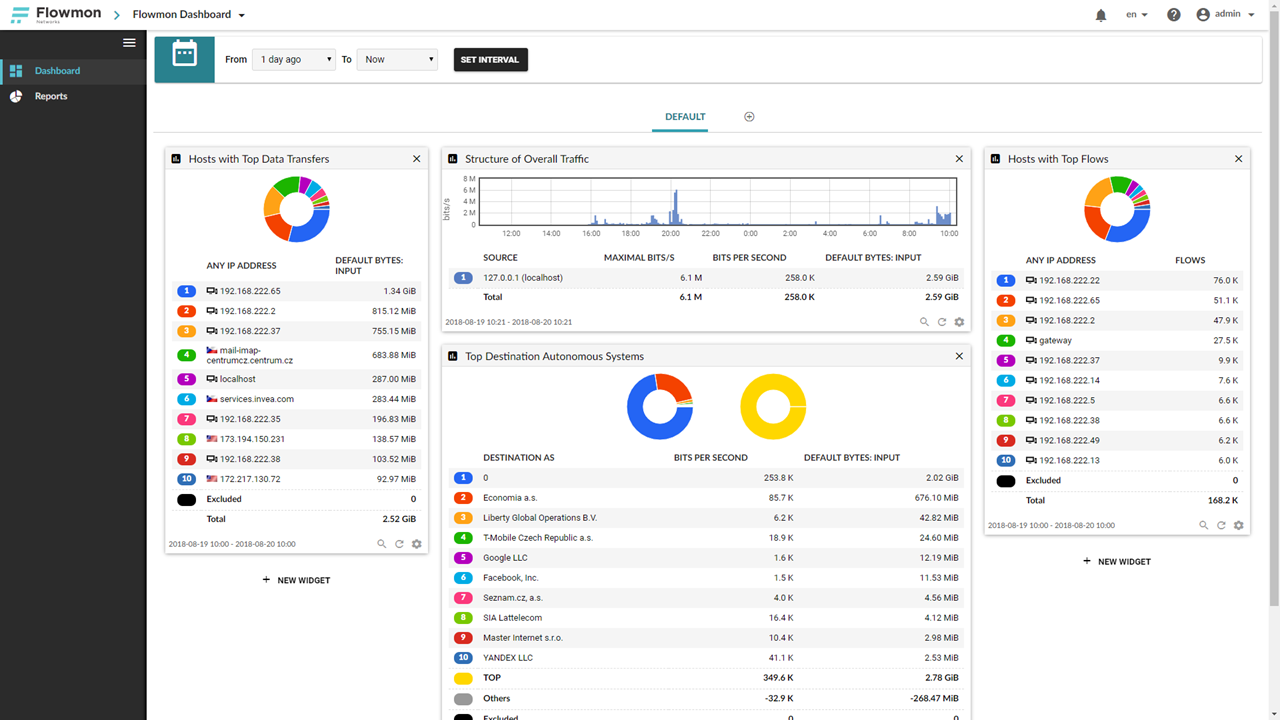
Figure 1: Flowmon 10.0 beta, revised UX - Flowmon Dashboard.
Distributed Architecture
A single enterprise benefiting from dozens of Flowmon deployments all across the globe, monitoring millions of flows per second. All managed with a single system. Meet the Flowmon Distributed architecture.
The whole distributed system is controlled by a special dedicated Flowmon appliance called “Master Unit”. Full redundancy is ensured by having multiple “Master Units” in place. Flow collection and processing happens in individual locations on “Slave Units”, which are standard Flowmon Collectors. Aggregated results, reports and dashboard data is delivered to the “Master Unit”. To scale up to individual locations, the “Proxy Unit” is used to distribute flow data among multiple “Slave Units” and manage their configuration. High Availability is achieved via a set of two (or even more) identical groups of appliances deployed in individual locations.
More details can be found in Distributed Architecture Overview document.
Figure 2: Sample scheme of distributed architecture composed of three groups in different locations controlled via “Master Unit”.
Encrypted Traffic Analysis Improves Security
According to Google Transparency Report, by the 22nd Sept 2018, 86% of internet traffic had been encrypted. Botnet command & control communication and malware activities benefit from the current boom of traffic encryption and hide within it. If your Windows 10 laptop suddenly starts communicating using a deprecated encryption algorithm in the SSL layer, you can be sure that such a device is compromised. What if your users communicate to servers with untrusted certificates? What is your current level of visibility into SSL/TLS traffic? Flowmon with release 10.0 redefines visibility into encrypted traffic. Without the need to breach user privacy you can report on various characteristics of encrypted traffic, including protocol version, encryption algorithm, cipher suite or certificate details. Moreover, Flowmon supports JA3 fingerprint, designed to recognize malicious clients in the network based on their overall SSL/TLS characteristics. Encrypted traffic analysis is the key technology to cope with the latest threats and discover network compromise.
Native Monitoring of IoT/ICS environments
As ICS (Industry Control System) and traditional IT is merging using ethernet and IP-based communication, responsible administrators are faced with new operational, but also security tasks. With version 10.0, Flowmon comes with new features and capabilities to extend the monitoring of the native IoT environment (represented by the CoAP protocol) and the ICS/SCADA environment in energy distribution technology networks (represented by the IEC 104 protocol). Such visibility goes beyond flow level and reveals critical information from the application layer showing executed commands or even transmitted data, thus delivering much better value than much more complex and less scalable packet capture solutions.