Ransomware is the gift that keeps on giving. Old as it is (33 years) ransomware is constantly morphing into new exploits. The reason is simple. Ransomware works and too often cybercriminals walk away with bags of money (or piles of Bitcoin, anyway).
“Following the World Health Organization's AIDS conference in 1989, Joseph L. Popp, a Harvard-educated biologist, mailed 20,000 floppy disks to event attendees. The packaging suggested the disk contained a questionnaire that could be used to determine the likelihood of someone contracting HIV,” explained TechTarget in The History and Evolution of Ransomware.
The attendees got a rude surprise after loading the disk, as the below screenshot shows.
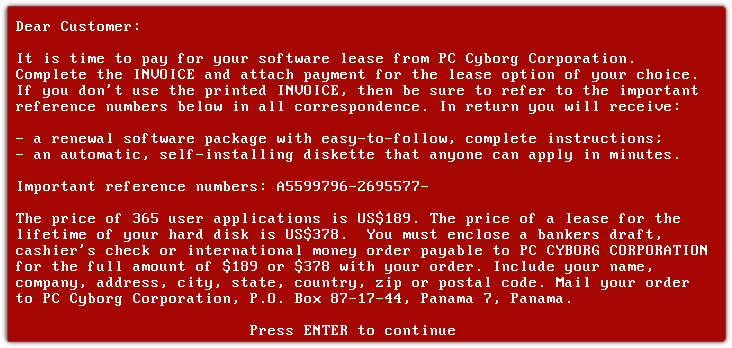
Ransomware continues to evolve, becoming more dangerous, devious and widespread. Nowadays, untalented hackers can even buy into Ransomware as a Service and make money without lifting a finger.
Success (meaning victims pay the ransom) only breeds more attacks. Cybernews.com, in its Top Cybersecurity Threats of 2022 Report, argues it is not always a good idea to pay off the ransomware creeps. “There has been much debate over the effectiveness of paying a ransom between pundits. While many insurance companies opt for paying, experts suggest that such decision does not only fuel cybercrime, but also doesn’t guarantee the return of data,” the site advised.
Ransomware Protection Better than Ransomware Cleanup
Instead, IT should stop ransomware from happening in the first place or have ways of protecting the data so even if it is encrypted, there are current backups that are not frozen or corrupt. “It is like a burglar going through the neighborhood—they are not going to attack a house that probably has bars on the windows as much as the one that looks like a much easier target to penetrate,” Jack O'Meara from Guidehouse told CyberNews.
The Stunning Cost of Ransomware – Even If You Don’t Pay the Ransom
Ransomware, by freezing your data, inflicts massive economic carnage. “The Sophos State of Ransomware Report 2021 shows that the average cost to deal with an attack in 2021 was $1.85 million. This was up from the 2020 average of $761,106. These costs cover all the activities required to recover from a ransomware attack. Including paying the ransom, the costs associated with business disruption when IT systems are unusable, operational downtime for machinery and other plant devices usually controlled by IT systems, staff overtime payments during the recovery period, and more. Within the 2021 figures, the actual ransom payment average was only $170,404. So even if an organization decides not to pay this and recovers via other means, the costs will still be high. Preventing ransomware attacks is a better solution!” argued Frank Yue in his What is Ransomware and How Do I Stop It? blog.
Stopping Ransomware Before It Goes Too Far
Unlike some attacks, ransomware is not instantly obvious, and this critical juncture CAN and SHOULD be used for detection and mitigation. “There may be a delay when the ransomware does nothing to avoid detection before it activates, and then another delay before cybersecurity professionals detect the ransomware’s activity. This period is known as the dwell time, and it can be months for some malware types. For ransomware, however, dwell time is typically measured in weeks as one of the activities that ransomware does is so disruptive – namely encrypting an organization’s data,” explained the What is Ransomware and How Do I Stop It? blog.
The Flowmon Ransomware Answer
Flowmon Anomaly Detection System (ADS) from Progress Software offers network detection and response leveraging an AI-powered engine that can spot the footprints of an ongoing ransomware attack in the early stages – before the data is even encrypted and a ransom demanded.
“It helps security leaders to cover visibility gaps by monitoring east/west traffic, understand the problem and respond manually or automatically before the ransomware starts spreading across digital assets and harms the business,” explained Frank Yue in his What is Ransomware and How Do I Stop It? blog. “You can minimize the impact of a ransomware attack by spotting it early. Flowmon monitors and analyzes network traffic to alert you to security compromises at early stages so that you may act before the danger escalates.”
Visibility into anomalies and other ransomware indicators lets security pros know when something is going wrong and that ransomware has made it into the network. Once known, IT can literally track the attackers’ footprints across the network.
“The solution does not use just one detection mechanism, but several, all working at the same time, including machine learning, heuristics, behavior patterns, adaptive baselining, reputation databases, and signature-based detection. They cover a wide number of scenarios by examining the network from several points of view. For instance, threats that would escape detection by reputation databases will be revealed by entropy modeling. Because the solution uses network traffic metadata for its analysis,” the Yue blog argued.
The Customer View
Flowmon customers see the early detection benefit. “Thanks to Flowmon we are able to reveal threats and malicious behavior within the internal network. And in the most important experience - we have significantly reduced incident resolution times,” said Flowmon customer Vittorio Cimin, CIO of Bricofer.
Three Ways to Defang Ransomware
1. Set Up for Quality Backups
Ransomware succeeds by encrypting critical business or organization data. But what about backups? Indeed, PROPER backups could make it all go away. The trick is to have backups that are current enough to be useful and disconnected enough from the primary data that the backup itself is not corrupted.
2. Keep Network Perimeter Protection Up to Snuff
While ADS and network monitoring are key ransomware defenses, they are part of an overall in-depth defense strategy with layers of protection. “Perimeter defense via firewalls, intrusion detection systems, security-enhanced load balancers, and other network infrastructure devices (physical and virtual) have provided the foundation layer for cybersecurity for years. They are still vital and must be part of any comprehensive cybersecurity strategy. It is essential that all perimeter network devices are up to date with the latest operating systems and security patches. If any items are out of support and not getting updates, then a plan to replace them should be drawn up and implemented as soon as practicable,” the What is Ransomware and How Do I Stop It? blog stated.
“Firewalls can prevent unauthorized outward data flows to any unknown IP addresses on the Internet — a common practice in modern ransomware attacks. Of course, firewalls are still vital to block unwanted inward connection requests too. Web Application Firewalls (WAFs) should also be deployed, on Progress Kemp LoadMaster for example, as they provide additional traffic analysis and defense options at multiple layers of the network stack.”
3. Use Network Detection Tools
Hackers are experts in defeating layered defenses, which is why specific tools to detect the out of the ordinary are so critical. “The Progress Flowmon Anomaly Detection System (ADS) is a machine learning-based solution that monitors networks in real-time to detect the anomalous network activity that unauthorized users generate. It uses over 40 detectors for various attack activities and methods, combined with over 200 algorithms that use heuristics, machine learning, and other techniques to analyze the data collected by the detectors. See this blog post and the technical articles linked from it for more information,” the blog said.
Flowmon Anomaly Detection System (ADS) To the Rescue
Ransomware moves laterally across both endpoint devices and servers, so in essence the malware travels across the network and in this sense can be tracked, found and ultimately stopped.
One common ransomware technique is using Remote Desktop Protocol (RDP) to attack nodes on the network. To connect to remote systems and crack them via RDP, ransomware indexes common password lists to guess the actual login credentials. While too often successful, this approach leaves breadcrumbs in the form of multiple failed login attempts. Fortunately, ADS boasts RDPDICT, a monitoring service that finds and alerts on unusual numbers of failed RDP login attempts.
Discovering ransomware’s lateral moves quickly allows for fast remediation action and vastly minimizes damage.
Spot Ransomware Early
Learn how network visibility from Flowmon helps detect and stop ransomware early in our Ransomware Detection page.