Zero trust isn’t an approach that can be delivered by buying a single product that claims to provide it. Instead, it is an approach that needs to be understood and implemented in complementary ways across an organization’s IT systems.
We recently hosted a webinar titled Applying Zero Trust to Data Centre Networks to provide guidance on how organizations can use zero trust to enhance the security of their IT systems. The webinar details are below, after a summary of the topics covered.
What is Zero Trust?
Zero trust is a concept that industry analysts coined at the start of the 2010s as a way of discussing and finding answers to the cybersecurity threat questions that were emerging. Zero trust is defined by a set of principles, but it is not a framework you can follow (for completeness, it’s worth pointing out that the term Zero Trust Network Access (ZTNA) is often used interchangeably for zero trust).
During the webinar, Nicolas Blank (CEO of NBConsult Group and a Microsoft MVP) outlined what zero trust is and the issues it’s intended to address. He pointed out that zero trust isn’t a framework, so you can’t be zero trust compliant. Then outlined that zero trust uses a set of principles that organizations can follow that cover Identity, Endpoints, Data, Apps, Infrastructure, and Networks.
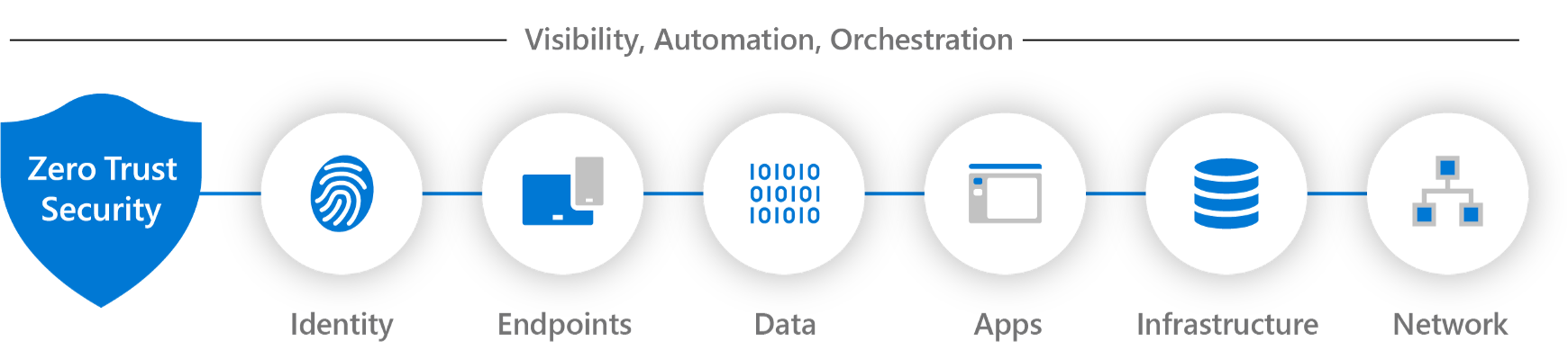
Figure 1: The Six Zero Trust Security Principles
Implementing zero trust across these six principles requires that each connection gets treated as hostile. Implementing this requires that you assume a breach, use least privilege access controls, and explicitly verify all connections and activities.
Zero Trust for Microsoft Customers
During the webinar, Nicolas also outlined the extensive (and growing) documentation library available from Microsoft delivering advice on starting with and implementing zero trust across Microsoft’s technology platforms. As part of this documentation project, Microsoft has developed a Zero Trust adoption framework modeled on its successful Cloud adoption framework.
The Zero Trust adoption framework provides the information needed to convince leadership teams in organizations from the C-Suite and downward why Zero Trust is needed and to justify the resources required to implement it properly. Nicolas concluded by discussing how to approach the implementation of Zero Trust, starting with strong identity management, good Endpoint and other system security with Microsoft Defender, and how policies and threat protection solutions are essential.
Zero Trust & Networks
Internal network activity needs to be treated as if breached and hostile for zero trust to be effective. The Microsoft Zero Trust adoption framework leaves a gap in the data center network aspect of cyber defense. In the webinar, Filip Černý (Product Marketing Manager for Progress Flowmon) outlined how Flowmon NDR (Network Detection and Response) solutions can plug this gap and enable organizations to maximize their zero trust-based protection.
Filip outlines why monitoring for abnormal network activity is essential and how NDR fits into the Gartner Security Operations Center (SOC) Visibility Triad with SIEM (Security Information & Event Management) and EDR (Endpoint Detection & Response). Filip then discusses why monitoring the network activity separately from perimeter security solutions such as firewalls and Endpoint protection is crucial to identifying all threats.
Flowmon Network Detection & Response
The Flowmon solutions portfolio is outlined briefly during the webinar. Then it takes a deeper dive into Flowmon NDR to outline how it works and why it goes beyond simple pattern-matching solutions.
While some companies may label what they are doing as AI, Flowmon maintains that AI is simply a means to an end. The goal is to provide relevant telemetry and forensic data stripped of general network noise to enable human security analysts to see important events and respond appropriately.
Filip also covers how Flowmon NDR works with other cybersecurity tools like SIEM systems and then outlines how defenders can use NDR to spot and contain a typical ransomware attack.
Watch the Webinar to Get the Details

