
Flowmon Helps to Comply Various Cybersecurity Regulations
Cybersecurity compliance encompasses rules and regulations that businesses must comply with for responsible and legal operations.
Launch demo

Flowmon Helps to Comply Various Cybersecurity Regulations
Compliance and regulation are rules and legislative frameworks that businesses must follow to operate ethically, legally, and responsibly.
Global scale economy, its self-interconnection and the growth of cyber threats that threaten the availability of services, the integrity of systems and the confidentiality of data are increasing on yearly basis. It is not just about sophisticated cyber-attacks, but also human errors associated with the configuration of the IT environment, non-application of basic security policies in organizations, or insufficient user awareness. That all is reason governments are also trying to mitigate the risks associated with this in the form of various legislative measures.
Compliance and Regulation Overview
There are many legislative measures and we can divide them into three areas. The first is international regulation, which is superior to national legislation and regulated entities must follow the given regulation (e.g. GDPR). The second, we have various national legislative measures (laws), which may differ from country to country. Third one are international directives (e.g. NIS2, RCE, DORA), which are kind of general framework for creation of national legislative measures. Individual countries are obliged to transpose these directives in their national legislation, in the form of laws and/or executive decrees and/or recommendations. Nationally competent authorities (e.g. NSA) are responsible for supervising of that obligations arising from these legislative frameworks. According to this legislative framework, the following regulated entities apply compliance measures.
Fulfill cybersecurity compliance and regulation standards, including data protection, incident prevention and breach reporting obligations with Flowmon’s intelligent network monitoring and analysis.
What is NIS 2 Directive?
The Network and Infrastructure Security (NIS 2) Directive (effective since Dec 2022) is an update to the original NIS Directive (effective since July 2016) and aims to strengthen the cybersecurity resilience for EU Member States. It sets out new rules for managing cyber risks, incident reporting, and cooperation between EU Member States, among other things. The directive covers a wide range of essential and important entities, including energy, transport, banking, healthcare, and digital infrastructure. Its main goal is to ensure that infrastructure of operators of essential and important services have appropriate security measures in place to prevent their systems and data from cyber security incidents as well as they would be able to respond and report effectively to any significant incident that occur.
What is the high-level timeline?
The NIS 2 Directive was adopted by the European Parliament and Council in December 2022 and EU Member States have until October 17th 2024 to transpose it into their national legislation framework.
By 17 October 2024, Member States shall adopt and publish the measures necessary to comply with this Directive
T+22mnthsT+31mnthsT+41mnthsT+45mnths
T = effectiveness of NIS 2 (Jan 2023)
Regulated essential and important entities
Preparation
Registration
Measures
Obligations
Audit
I am an Essential or Important Entity. What Does NIS2 Mean for me?
As an essential and important entity, the NIS 2 Directive means that you are subject to specific cybersecurity risk management requirements designed to protect your infrastructure from cyber threats. The directive requires you to implement appropriate security measures to prevent cybersecurity incidents and to report any significant incidents that occur to the relevant national competent authorities. It also encourages cooperation and information-sharing between EU Member States and relevant stakeholders to enhance overall cybersecurity to ensure service availability, system integrity and data confidentiality.
1. Preparation
During this period till NIS 2 will be transposed into National Legislation framework all potential essential and important entities would follow mainly Article 21 of NIS 2 and provide Risk Analysis, GAP Analysis and Business Impact Analysis if they have implemented all minimum measures described in that Article based on Asset Inventory.
2. Registration
After National Legislation effectiveness National Competent Authority will require registration of all regulated entities (described in ANNEX I and II of Directive) and their list of essential and important services based on specific § criteria of National Legislation, but at least till Jan 17th 2025. National Legislation will have definitely wider scope of requirements need to be met than is described in directive.
3. Measures
- Policies on risk analysis and information system security
- Incident handling
- Business continuity, backup management and disaster recovery, crisis management
- Supply-chain
- Network security and vulnerability handling and disclosure
- Policies and procedures to asses measures
- Basic cyber hygiene and awareness
- Cryptography and appropriate encryption
- Human resources security, access control and asset management
- Multi-factor authentication
4. Obligations
- Detailed description, severity and impact
- The type of threat or root cause of triggered incident
- Applied mitigation measures
- Where applicable, the cross-border impact
5. Audit
Based on specific & criteria of National Legislation supervisory National Competent Authority of enforcement measures in respect of the obligations of regulated entities will require to provide regular or ad hoc and targeted security audits carried out by an independent body or a competent authority. In case of ineffectiveness of results regulated entities will need to take appropriate action to remedy or will be sanctioned.
I am a CSIRT. What Does NIS2 Mean for me?
Each Member State shall designate or establish one or more CSIRTs within a National Competent Authority for ensuring high availability communication channel with regulated entities and other third countries CSIRTs for information sharing. Moreover CISRTs shall be equipped with an appropriate redundant system for managing a routine requests to ensure continuity of their services and shall promote the adoption and use of common or standardised practices, classification schemes and taxonomies regarding incident handling procedures, crisis management and vulnerabilities disclosure. Based on specific § criteria of National Legislation CSIRTs shall follow these particular tasks:
- Monitoring and analyzing cyber threats, vulnerabilities and incidents at national level.
- Upon request providing assistance to essential and important entities concerned regarding real-time or near real-time monitoring of their network and information systems.
- Providing early warnings, alerts to essential and important entities concerned as well as to the competent authorities on cyber threats, vulnerabilities and incidents in real-time.
- Responding to incidents and providing assistance to the essential and important entities.
- Collecting and analyzing forensic data and providing dynamic risk and incident analysis.
- Providing, upon the request of an essential or important entity, a proactive scanning of the network and information system to detect cyber threats.
How Can Flowmon Help you be NIS 2 Compliant
Flowmon is a comprehensive intelligent network security monitoring solution that provides real-time visibility into network traffic and helps organizations detect cyber threats and respond to cyber incidents. This directive is all about security of network and information systems to resist to any event that may compromise the availability, authenticity, integrity or confidentiality of data or services transmitted through network.
Here's how Flowmon can help you achieve NIS 2 compliance:
Threat Detection and Threat Hunting
NIS 2 requires organizations to have an "early warning mechanism" to detect and respond to cyber threats. Flowmon uses advanced algorithms to analyze network traffic in real time, detect anomalies and indicators of compromise (IoCs), incl. 0-Day vulnerabilities. This helps regulated entities and CSIRTs identify potential threats early and take proactive action to prevent them from cyber security incident.
Digital Forensics and Incident Reponse
NIS 2 requires organizations to have incident handling and management on place to minimize the impact of cyber security incidents. In the event of a security incident, Flowmon provides automated detection and analysis to containment. Moreover, Flowmon collect all data for months and years for digital network forensic that can be used to identify footprints of triggered incident. This helps regulated entities fulfill whole incident handling process and get appropriate information for Incident Reporting obligations.
Hybrid Cloud Monitoring and Encrypted Traffic Analysis
NIS 2 requires organizations to have "comprehensive monitoring" of their hybrid networks to analyze essential and important services availability and functionality. Flowmon provides visibility into encrypted traffic and ensure regulated entities has implemented appropriate encryption procedures and also detect and respond on hidden threats within encrypted traffic.
Root Cause Analysis and Performance Monitoring
NIS 2 requires regulated entities and CSIRTs to collect and analyze data when cyber incident occur. That "provide competent authorities with evidence" of structure of digital footprints within national network traffic. Complete visibility into traffic, including real-time monitoring of network and application performance allows regulated entities and CSIRTs identify unusual activity on their networks and take action before it becomes a problem with services availability, systems integrity or data confidentiality.
It also encourages cooperation and information-sharing between EU Member States and relevant stakeholders to enhance the overall cybersecurity of EU cyber infrastructure.
ECC (SA) Quick Links:
- What is the Kingdom of Saudi Arabia's Cyber Security regulation?
- NCA developed 3 main cybersecurity controls within years 2018 – 2020:
- Structure of cybersecurity controls?
- I am SRE. What does these regulations mean for me?
- How can Flowmon help you be ECC (CSCC, CCC) compliant
- Download a Compliance & Regulatory for Saudi Arabia Datasheet
What is the Kingdom of Saudi Arabia’s Cyber Security regulation?
The National Cybersecurity Authority (NCA) established as part of the Kingdom of Saudi Arabia’s 2030 Vision is the central authority responsible for overseeing cybersecurity in Saudi Arabia. It plays a crucial role in formulating policies, guidelines, and regulations to protect critical infrastructure and mitigate cyber threats. Its mandate was approved as per the Royal Decree number 6801, dated 11/2/1439H making it the national and specialized reference for matters related to cybersecurity in the Kingdom.
NCA developed 3 main cybersecurity controls within years 2018 – 2020:
NCA developed 3 main cybersecurity controls within years 2018 – 2020:
-
ECC (1:2018): Essential Cybersecurity Controls are a set of guidelines and requirements issued by the NCA. These controls provide a framework for organizations to enhance their cybersecurity posture and protect critical information infrastructure. They cover various aspects of cybersecurity, including governance, risk management, access controls, incident response, and security monitoring. It contains:
- 5 Cybersecurity Main Domains
- 29 Cybersecurity Subdomains
- 114 Cybersecurity Controls
Subject Regulated Entities (SREs) are the entities that are subject to the Essential Cybersecurity Controls in Saudi Arabia. SREs include:
- Critical Infrastructure Operators: These are entities that operate and maintain critical infrastructure sectors such as energy, water, transportation, healthcare, finance, and telecommunications. Examples of critical infrastructure operators include power plants, airports, hospitals, banks, and telecommunications providers.
- Government Agencies: Government entities at the federal and local levels are also considered subject regulated entities. This includes ministries, agencies, and other government organizations that handle sensitive information or provide critical services.
- Digital Service Providers: Certain entities that provide digital services are subject to the Essential Cybersecurity Controls. These include cloud service providers, managed security service providers, domain registrars, and other entities involved in the provision of digital services.
-
CSCC (1:2019): Critical Systems Cybersecurity Controls as an extension of ECC specifically tailored to safeguard critical systems and infrastructure. These controls aim to protect critical infrastructure sectors such as energy, water, transportation, healthcare, finance, and telecommunications against cyber threats. CCC consists of the following:
- 4 Main Domains
- 21 Subdomains
- 32 Main Controls
- 73 Sub-Controls
Subject Regulated Entities (SREs) in the context of Critical Systems Cybersecurity Controls typically include organizations and entities that own, operate, or are responsible for critical systems and infrastructure. The specific entities can vary, but commonly regulated entities can include:
- Critical Infrastructure Operators: Entities operating critical infrastructure sectors such as energy, water, transportation, healthcare, finance, and telecommunications are subject regulated entities. Examples of critical infrastructure operators include power plants, oil refineries, water treatment facilities, transportation networks, and healthcare providers.
- Government Agencies: Government entities at the federal and local levels that are responsible for critical systems and infrastructure are subject to the Critical Systems Cybersecurity Controls. This includes ministries, agencies, and other government organizations that handle critical systems, such as defense systems or emergency services.
- Industrial Control Systems (ICS) Operators: Organizations that own or operate industrial control systems used in critical infrastructure or industrial processes are subject regulated entities. These systems include supervisory control and data acquisition (SCADA) systems, distributed control systems (DCS), and other operational technology (OT) systems.
-
CCC (1:2020): Cloud Cybersecurity Controls as an extension of ECC contains specific guidelines and controls for ensuring the secure adoption and usage of cloud services in Saudi Arabia. These controls focus on protecting sensitive data and mitigating the risks associated with cloud computing. It consists of the following:
- 4 Main Domains
- 24 Subdomains
- 37 Main Controls for CSPs and 18 Main Controls for CSTs
- 96 Sub-Controls for CSPs and 26 Sub-Controls for CSTs
Subject Regulated Entities (SREs) in the context of Cloud Cybersecurity Controls typically include organizations and entities that utilize cloud services. The specific entities can vary, but commonly regulated entities can include:
- Cloud Service Providers (CSPs): Cloud service providers that offer services in Saudi Arabia are also subject regulated entities. These are the entities that provide cloud infrastructure, platforms, or software services to customers. They are required to comply with the Cloud Cybersecurity Controls to ensure the security of their cloud offerings.
- Cloud Service Tenants (CSTs): Any government organization in the Kingdom of Saudi Arabia inside or outside the Kingdom (including ministries, authorities, establishments and others) and its companies and entities, as well as private sector organizations owning, operating or hosting Critical National Infrastructures (CNIs) that currently use or planning to use any cloud service.
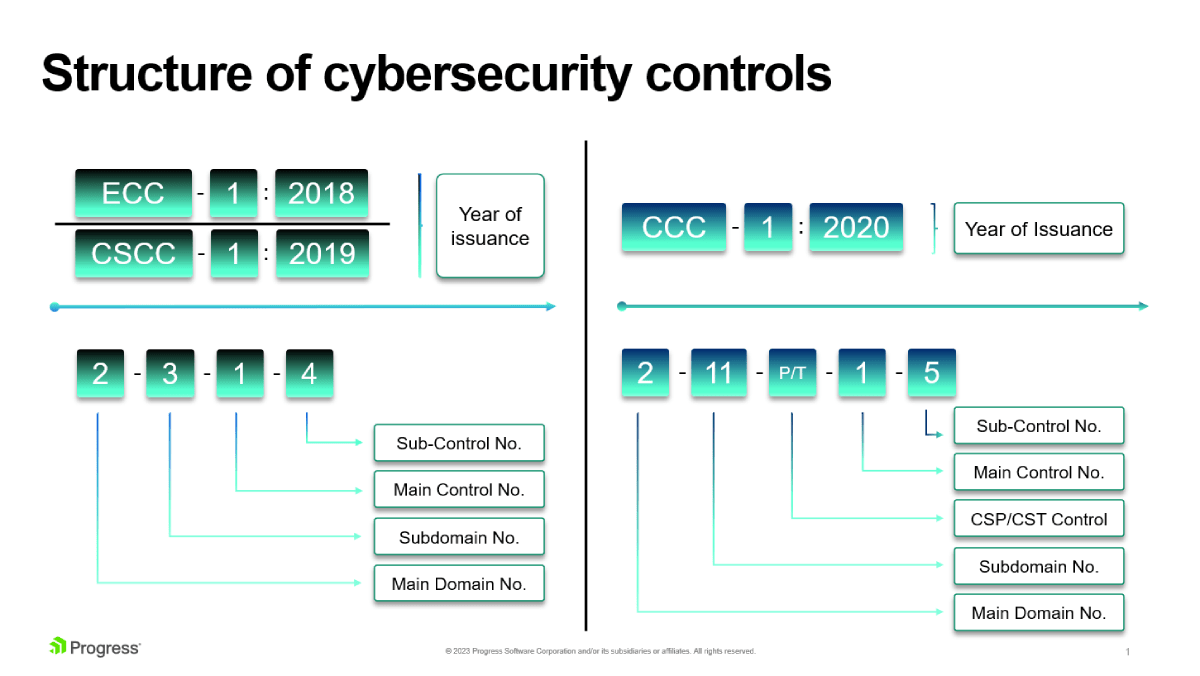
Structure of cybersecurity controls?
Cybersecurity controls defines key objectives must be focused on in order to protect the organization’s information and technology assets – Confidentiality, Integrity and Availability. These controls take into consideration the following four main cybersecurity pillars – Strategy, People, Processes and Technology.
Structure definition of all Domains, Subdomains, Controls and Sub-Controls contains these fundamental measures need to be implemented and be following NCA regulations:
- Cybersecurity Governance
- Cybersecurity Defense
- Cybersecurity Resilience
- Third-Party (and Cloud Computing) Cybersecurity
- ICS Cybersecurity
I am SRE. What does these regulations mean for me?
As an SRE means that you are subject to specific cybersecurity requirements designed to protect your infrastructure from cyber threats. The regulation requires you to implement appropriate security measures to prevent cybersecurity incidents and to report significant incidents that occur to the NCA and The ECC requires the appointment of a “Competent Person” to ensure the organization’s cybersecurity strategy is full in compliance with these regulations.
-
Cybersecurity measures – Although the measures within the framework of ECC and their extension CSCC and CCC are similar, they differ in structure and designation, and in some cases, they also differ in individual measures.
-
Essential Cybersecurity Controls (ECC):
- Risk Assessment and Management: Organizations are obliged to conduct risk assessments to identify potential cybersecurity risks and vulnerabilities. They must develop risk management processes and implement appropriate controls to mitigate these risks effectively.
- Incident Response and Reporting: Organizations are required to establish incident response plans and procedures to detect, respond to, and recover from cybersecurity incidents. They may be obligated to report significant incidents to the National Cybersecurity Authority (NCA) or other regulatory bodies.
- Access Controls and Authentication: Organizations must implement robust access controls and authentication mechanisms to ensure that only authorized individuals can access systems and sensitive data.
- Security Monitoring and Logging: Organizations should have mechanisms in place to continuously monitor and log security events and incidents. This helps in detecting and responding to potential threats in a timely manner.
- Employee Awareness and Training: Organizations are encouraged to provide cybersecurity awareness and training programs to their employees to enhance their understanding of cybersecurity risks and best practices.
-
Critical Systems Cybersecurity Controls (CSCC) as an extension to ECC based on Critical Systems Identification Criteria:
- System Segmentation and Access Controls: Organizations operating critical systems are obligated to implement network segmentation and access controls to protect these systems from unauthorized access and potential exploitation.
- Identity and Access Management: Robust identity and access management measures must be in place to ensure that only authorized individuals can access critical systems.
- Physical Security Measures: Organizations should implement physical security measures to protect critical systems and infrastructure from physical threats and unauthorized access.
- Threat Intelligence Sharing: Organizations operating critical systems are encouraged to collaborate and share threat intelligence to enhance their cybersecurity readiness and response capabilities.
-
Cloud Cybersecurity Controls (CCC) as an extension to ECC:
- Data Protection and Privacy: Organizations utilizing cloud services must ensure the protection and privacy of sensitive data stored or processed in the cloud. Measures such as encryption and access controls should be implemented.
- Secure Configuration of Cloud Services: Organizations are obliged to configure cloud services securely to minimize vulnerabilities and risks.
- Incident Response and Recovery in Cloud Environments: Organizations must have specific incident response and recovery plans for cloud-based incidents, ensuring effective handling and recovery from security breaches or disruptions.
- Continuous Monitoring of Cloud Environments: Organizations should establish mechanisms to continuously monitor the security of their cloud environments to detect and respond to potential threats promptly.
-
Essential Cybersecurity Controls (ECC):
- Audit – NCA evaluates organizations’ compliance with the ECC through multiple means such as self-as- sessments by the organizations, periodic reports of the compliance tool or on-site audits.
How can Flowmon help you be ECC (CSCC, CCC) compliant
How can Flowmon help you be ECC (CSCC, CCC) compliant
Flowmon is a comprehensive intelligent network security monitoring solution that provides real-time visibility into network traffic and helps organizations detect cyber threats and respond to cyber incidents. All these regulations require (2) Cybersecurity Defense as an important domain to leverage overall SREs (3) Cybersecurity Resilience, (4) Third-Party and Cloud Computing Cybersecurity and (5) Industrial Control Systems (ICS) Protection.
Here's how Flowmon can help you achieve (2) Cybersecurity Defense Domain compliance trough main approaches like Threat Detection and Threat Hunting, Incident Response and Digital Forensics, Hybrid Cloud Monitoring and Encrypted Traffic Analysis and Root Cause Analysis and Performance Monitoring in single pane of glass for:
- Subdomain Networks Security Management ensures the protection of organization’s network from cyber risks. Flowmon provides continuous monitoring and compliance audit if all controls are implemented in proper way, detection of behavioral anomalies, attacks, suspicious and malicious traffic communication and security policies violation within Controls 2-5-3 (ECC), 2-4-1 (CSCC) and 2-4-P-1 (CCC).
- Subdomain Information System and Information Processing Facilities Protection within CSCC and Sub-Controls 2-3-1-4 requires allocating specific workstations in an isolated network (Management Network), that is isolated from other networks or services (e.g., email service or internet), 2-3-1-5 requires encrypting the network traffic of non-console administrative access for all technical components of critical systems and 2-3-1-8 requires protecting systems' logs and critical files from unauthorized access, tampering, illegitimate modification and/or deletion.
Flowmon continuously monitor critical assets and services, their network communications to ensure network segmentation is deployed properly. Moreover trough Encrypted Traffic Analysis (ETA) capabilities monitor ciphers suites, certificates or types of key algorithms. If any lateral movement of attacker inside critical infrastructure is happening, Flowmon detects unexpected behavior in real time, analyzes in autonomous way and responds immediately. - Subdomain Cryptography ensures the proper and efficient use of cryptography to protect information assets as per organizational policies and procedures regarding these regulations. Flowmon is able to monitor, check and audit if requested cryptography is used per organization, network segment, critical assets or services within Control 2-8-2 (ECC) and Sub-Controls 2-7-1-1 (CSCC), 2-7-P-1-1 and 2-7-T-1-1 (CCC).
- Subdomain Cybersecurity Event Logs and Monitoring Management ensures timely collection, analysis and monitoring of cybersecurity events for early detection of potential cyber-attacks in order to prevent or minimize the negative impacts. As Flowmon is using mainly for network monitoring of cybersecurity events (attacks, misconfigurations, user or network suspicious behavior, vulnerabilities, outages etc.) which forward within aggregated form directly to SIEM for advanced correlation. That helps to comply with Sub-Controls 2-12-3-3, 2-12-3-4 (ECC), 2-11-1-3, 2-11-1-4 (CSCC) and 2-11-P-1-5 (CCC). Moreover, Flowmon provides the most powerful IPFIX Collectors for long term data retention period which require Sub-Control 2-12—3-5 for 12 months (ECC) and Control 2-11-2 for 18 months (CSCC).
- Subdomain Cybersecurity Incident and Threat Management ensures timely identification, detection, effective management and handling of cybersecurity incidents and threats to prevent or minimize negative impacts. This is all about incident handling and response procedures where Flowmon plays crucial role in many phases related standards like NIST. It helps to be compliant with Sub-Controls 2-13-3-3, 2-13-3-4, 2-13-3-5 (ECC) and 2-12-P-1-4, 2-12-P-1-5, 2-12-P-1-6 (CCC). Developing incident response plans is part of Sub-Control 3-1-3-2 (ECC).
USE OUR SLIDE NIST INCIDENT REPONSE CYCLE
Although there are no penalties set out in the ECC all SREs must report all significant incidents to NCA (as a cybersecurity competent authority within Kingdom of Saudi Arabia) responsible also for education, training, and raising awareness about cybersecurity through establishing affiliated centers.
Download a Compliance & Regulatory for Saudi Arabia Datasheet.

Request free trial
Get no-obligation 30-day trial of Flowmon in your network.
Get your trial today