Throughout IT history, new technologies have been co-opted by bad actors and abused for malicious activities. And encryption is no different. Even though it might sound paradoxical, it is a well known fact that this security measure can also be a means of carrying cyberthreats. When we commissioned IDG Connect to conduct a survey among businesses to better understand encrypted traffic threat issues at the end of last year, the data showed us that today, 99% of IT professionals (IT management and C-levels) see encrypted traffic as a possible source of security threats.Our findings also show that a vast majority of respondents have some means of inspecting encrypted traffic. So far so good, it would seem, but upon a closer look at encryption monitoring technologies that are in use, things start to look bleak.
Detection toolset vs. attack vectors divergency
“Some” insight is one thing, but reliable detection is another. Especially when the increase in number of threats that misuse encryption (76% increase in 2019 according to SonicWall) accompanies the tendency of organizations to encrypt everything like an evil twin (87% of the entire web traffic is encrypted now according to Mary Meeker's Internet Trends report). Consider these statistics:
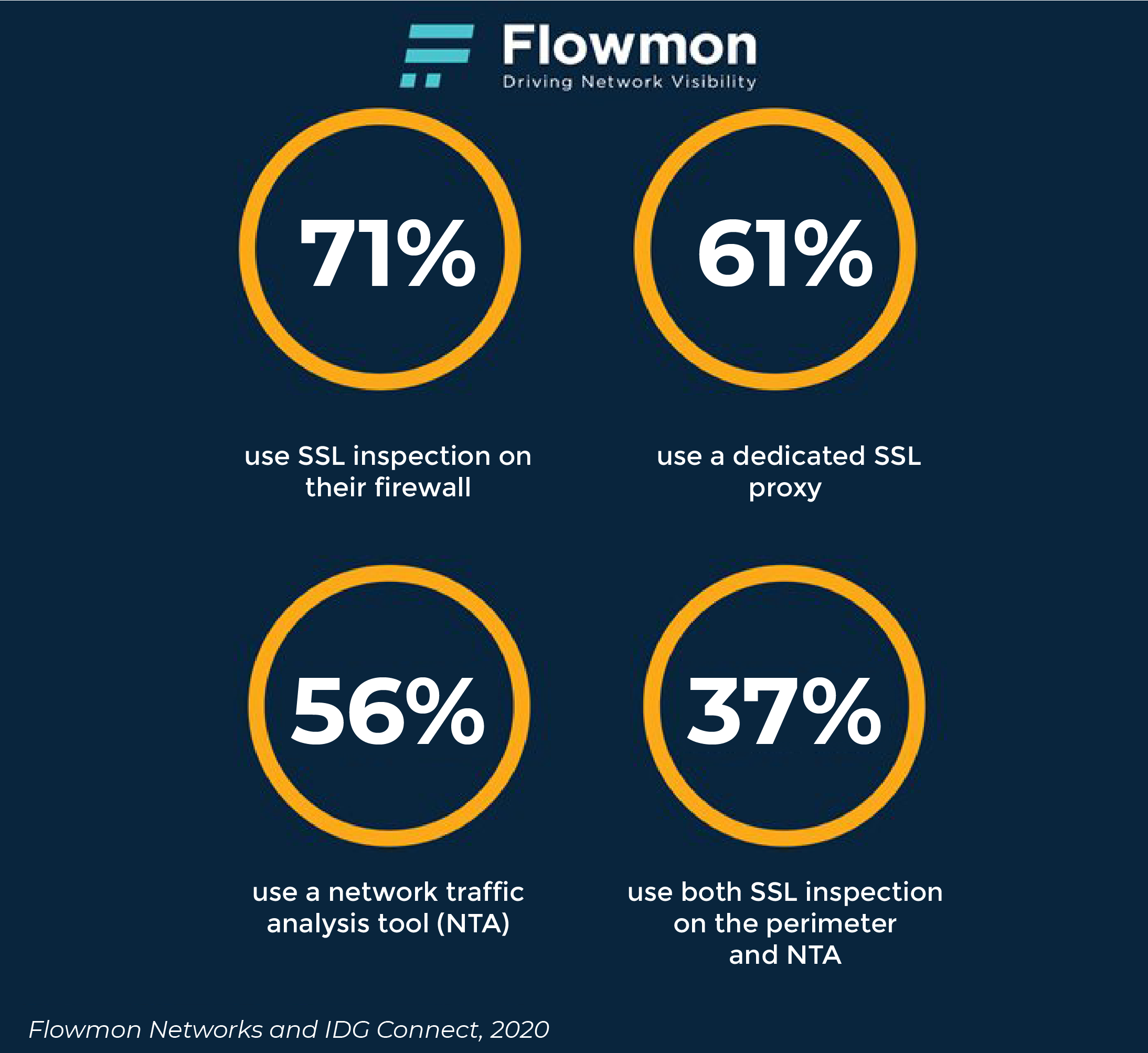
While some 96% of those polled say they feel quite confident, the truth may not be as bright as painted. The vast majority of respondents primarily inspects encrypted traffic at the perimeter, meaning they are unprotected from insider, unknown or advanced persistent threats (e.g. SSL/TLS vulnerabilities misuse, cloak malware delivery, hide data exfiltration, and mask botnet communications).Only one third of respondents have both perimeter and network protection deployed together. When common forms of attack avoid perimeter detection, such as ransomware, botnets obscuring communication with C&C servers, advanced persistent threats or browser exploits, there appears a considerable gap in the security strategies that businesses deploy.
Solutions must let NetOps talk to SecOps
We were also interested in what respondents expected from an encrypted traffic analysis (ETA) tool. By far the most cited answer was supporting NetOps and SecOps teams in cooperating (49%), followed by performance and rapid response to threats. This is a welcome verdict because having both teams working as one is the sign of a healthy and secure IT operation.Imagine a data exfiltration scenario where one station is periodically sending out large amounts of data. The unsuspecting user experiences this as a network performance issue and reports it to the networking team, who note nothing. As far as they know, the network is fine, but prudence dictates they refer this to the security team. It may be a minor matter, but it’s their job to check. The security team goes through their logs, but to their knowledge, the perimeter had not been compromised. And yet, a piece of unknown malicious code lives in the network, having snuck in under the guise of legitimate encrypted communication.
Data privacy concerns
Given the widespread use of SSL decryption in encrypted traffic monitoring, we wanted to know what concerns the respondents might have in connection with its deployment. A total of 70 % cited fears over the exposure of private sensitive data, out of which 33 % marked this as their biggest worry. This is a valid concern, as data exposure can lead to public controversy and even severe legal penalties.It is therefore no surprise that out of those who decided against deploying decryption, 36 % said it was due to data privacy concerns. It testifies to the fact that decryption, while undoubtedly powerful, is not risk-free and consequences may be dire if things do go wrong.
Conclusion
The dynamic rise of encrypted connections has provided bad actors with greater opportunities to misuse SSL/TLS vulnerabilities and to cloak malware delivery to users, hide data exfiltration, and mask botnet communications.Even though IT professionals claim confidence about their ability to fight encrypted traffic threats, only one third of respondents protect both perimeter and network from this growing attack vector. That’s something that needs to be addressed. Cooperation between network and security operations teams seems to be a legitimate fix. NTA solutions such as Flowmon should play a key role when ensuring this, delivering encrypted traffic analysis at a reasonable price, with no performance impact or sensitive data disclosure. They can greatly complement traditional SSL decryption tools, help to cover all attack vectors and reduce mean time to resolution by putting NetOps and SecOps teams together.More results of the survey focused on menace of encrypted network traffic threats and businesses ability to handle them are available in this report. Further reading: